Account takeover and concert tickets
- Reading time:
- 6 min
Taylor Swift and Account Takeover
What do the world’s most famous pop star and account takeover and data leaks have in common? And how can platforms protect their customers from the unexpected loss of concert tickets? Find that out here!
Finally Concert Tickets: From Anticipation to Frustration
Taylor Swift is probably the best-known and most popular pop icon in the world at the moment. Tickets for a concert can easily cost over €100, but can also easily break the €400 mark. And although Taylor Swift concerts now take place in huge stadiums with thousands of spectators, tickets are often not easy to come by. So fans with tickets can count themselves lucky!
It is all the more frustrating when the ticket is suddenly gone. This has recently happened to many fans in the United States, but also in Germany (only available in German): You get up in the morning, check your email inbox and realise that the tickets you’ve been waiting for so long have been passed on or sold back to the provider under your own account and name (presumably to be bought directly by someone else) - not a nice idea, but this has happened a lot.
All Due To Account Takeover
But how does this happen? How do criminals end up selling concert tickets in my name? A significant factor lies in the digitization of event ticket systems. Most tickets are no longer available in physical form; instead, they are sold and purchased through ticket shops. Typically, buyers need an account to manage purchases, sales, and ticket storage. This account is usually accessible via a combination of an email address and password. Therefore, anyone with the correct email and password combination can access the respective account.
Credential Stuffing
This is precisely what has happened in most cases of ticket takeovers. But how do criminals acquire the necessary information? To answer this, it’s essential to know that hackers exchange and trade login data obtained through phishing or data leaks in underground forums. The problem is exacerbated by the fact that many users employ the same login credentials across different online services. Even if a user changes the credentials for security reasons, those same credentials remain valid for numerous other online services. Criminals exploit this vulnerability by trying the obtained credentials on various platforms, such as a ticket shop. This method of acquiring valid login data is known as credential stuffing.
Credential Stuffing and Concert Tickets
As previously mentioned, certain tickets, like Taylor Swift tickets, are so valuable that it’s worth putting in considerable effort to obtain them. To identify who has managed to get tickets for a concert, it often suffices to check social media (Instagram reveals a lot about users’ hobbies). Once a potential victim is identified, a skilled hacker can easily access common data leaks. The found credentials can then be tested on the corresponding ticket shop, and due to the reusability of login data, this strategy works more often than one might think.
An even more dangerous type of data leak are leaks caused by so-called Stealer Malware. Stealer malware not only collects passwords, but also the URLs to the corresponding services where the password is used. In such cases, the criminal does not even have to try out the passwords by credential stuffing, but has the access data and URL directly available. If a stealer leak also contains the access data for a ticket shop, it is even easier to steal tickets.
Are Only Concert Tickets of Interest?
Of course, it’s not just concert tickets that are affected. The same method can also be used to steal tickets for football matches, trade fairs, festivals or even access data for car apps. Of course, this method can also be used to take over the account of any social media platform, online shop, lottery portal or insurance company. Under certain circumstances, this can have even worse consequences than losing a concert ticket. You can find out more about the general consequences of account takeovers here.
Preventing Account Takeovers
When customers of a platform fall victim to ticket or account takeovers, platforms often respond with explicit warnings about the issue of password reuse. However, it has never been easier for a platform to recognize and prevent password reuse, effectively protecting their customers from account takeovers.
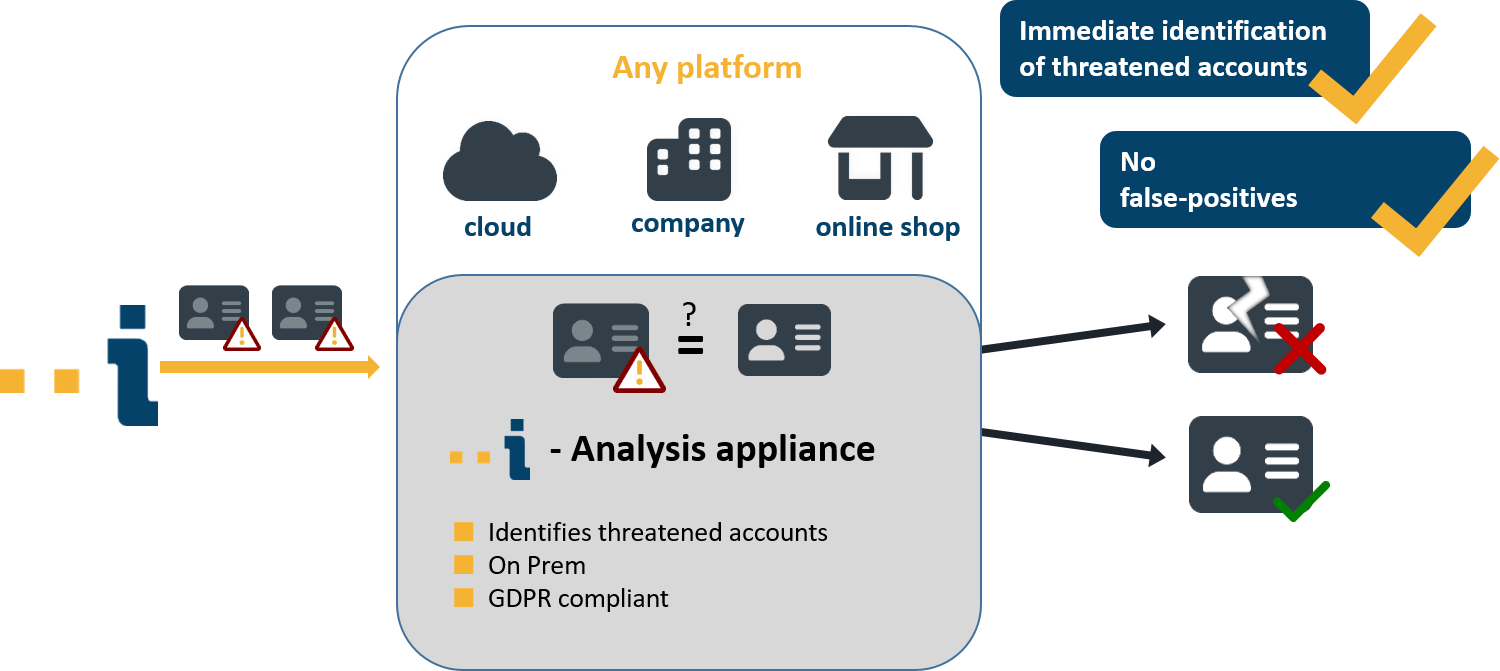
Platform Protection with Identeco
Identeco continuously collects the latest leaks and processes the contained data in compliance with GDPR. This data can then be made available to platforms to identify compromised login credentials. If an account is identified as being at risk from account hijacking, the account holder can be prompted through a second factor to choose a new password. This can specifically prevent unauthorized transactions, such as unwanted ticket sales, from being conducted through the affected account.
Protecting Accounts and Customer Relationships
An account is often the only relationship a platform has with its customers. And this relationship, like any successful relationship, must be nurtured. This includes protecting the account from account takeover and credential stuffing attacks, ensuring that the customer can continue to use the platform with peace of mind and that already purchased tickets remain in the hands of their rightful owner.
How to avoid Account Takeover and ensure Customer Protection
Avoid password reuse: Multiple use of the same access data for different services opens the door for criminals to access your own accounts through credential stuffing.
Credential stuffing: Criminals use captured credentials and try them out on many services to take over accounts and for example steal tickets.
Platform protection: Platforms can use Identeco products to identify compromised accounts and protect against account takeovers.
Strong customer relationship: Protecting customer accounts preserves customer trust and ensures a positive experience when using the platform.
Conclusion
Account takeover is a growing problem that not only leads to financial losses but also significantly damages the trusting relationship between platforms and their customers. This frustration is especially great with valuable items like concert tickets, which can be stolen through credential stuffing. However, platforms can actively contribute to protecting their customers by utilizing modern security technologies, such as Identeco’s products. By identifying and securing compromised accounts, account takeovers can be prevented, thereby preserving both the user experience and customer trust on the platform.
Here you can gain even more insight into the topics addressed:
If you have any further questions about data security, account security or Identeco’s services, please contact us at email or make an appointment with us here!


Artikel teilen