Phishing #3: Smishing, Vishing and Email Clone Phishing
- Reading time:
- 5 min

Phishing is a form of cyber attack in which attackers attempt to trick users into revealing sensitive information by pretending being a trusted source. There are different variants of phishing. In this blog post, we present three specific types of phishing: Smishing, Vishing and Email Clone Phishing. It thus continues our series on phishing: Phishing #1: Email Phishing, Baiting and Search Engine Phishing and Phishing #2: CEO Fraud, Corporate Phishing and Angler Phishing Attacks.
Smishing
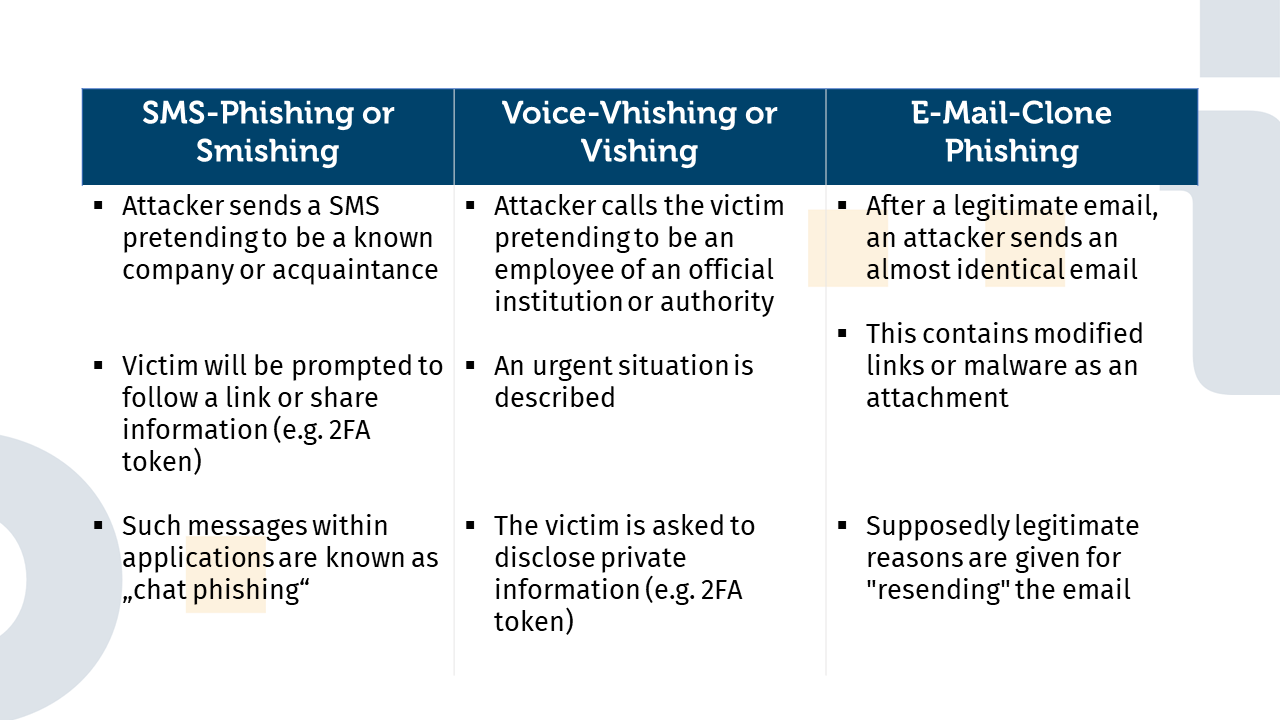
Smishing is a type of phishing attack carried out via SMS (Short Message Service). Attackers use fake SMS messages to trick users into clicking on links or revealing requested information. In many cases, the SMS message is worded to suggest urgency or a threat in order to alarm the recipient and pressure them to respond quickly. Often they try to appear like a well-known brand sending information about discounts or offers. Other attackers try to impersonate a regular known contact, suggesting a sense of familiarity to users. The main feature of smishing is the communication channel via SMS, but attackers also use the same type of attack in other applications where you can exchange chat messages. Smishing or SMS phishing differs from chat phishing, which usually only differs in the context or application in which the attacker’s message is received. A well-known example of smishing are fake SMS notifications from banks asking the recipient to urgently update their account details, to confirm or deny a suspicious transaction. In some cases, the SMS may also contain a link supposedly leading to an official website where the user is supposed to enter his or her data. The risk for victims is that they give sensitive information such as passwords, bank details or personal identification numbers (PINs) to the attackers. Victims may then suffer financial loss or identity theft.
Protection options and preventive measures against smishing
- Be careful replying to SMS messages received from unknown senders.
- Verify the content of the SMS with an official website or customer service before following a link or providing any requested information. If it is a supposed acquaintance, try to contact him or her via an already established communication channel or ask for shared knowledge.
- Never share passwords, PINs or similar security-related information.
Vishing
Vishing is a phishing technique carried out via VoIP (Voice over Internet Protocol) telephony. The attackers use phone calls to pose as trusted sources such as banks, government agencies or IT companies and try to get victims to reveal confidential information such as bank details or passwords. Questions are asked at the beginning that seem very harmless and are used to “verify” identity. Something like first and last name, birthday and place, address, etc. After that, depending on the situation presented, questions are asked about the bank account or insurance policies. Most people would start asking the attacker questions here at the latest. The attacker tries to pressure the victim into giving this information, e.g. by repeating how urgent the situation is. This lead to people feeling forced to give the information because the attacker triggers panic or fear in the victim.
A well-known example of vishing is calls from alleged IT support staff claiming that the victim’s computer is infected with viruses and requires immediate response. In some cases, the attackers may also claim that the victim has committed a crime in order to intimidate and force them to divulge information.
The risk for victims is that they may disclose sensitive information and subsequently suffer financial loss or identity theft.
Protection options and preventive measures against vishing
- Be sceptical of unexpected calls from unknown numbers
- Don’t be rushed e.g. you can take a minute break from the conversation to really think about what was said.
- Put the caller to the test: Even with harmless questions about “identity verification”, you can ask what information is already registered with the attacker. If he does not or “cannot” comment on this, try to deliberately insert small mistakes. These would be noticed by a legitimate caller, but probably not by an attacker.
Email Clone Phishing
Email Clone Phishing is a particularly insidious form of phishing attack that is often difficult to detect. In this attack, the attacker uses an email previously sent by a legitimate sender as a template for a fake email that is sent to the recipient. The attacker pretends that the email has been resent because the recipient base has been expanded or for some other supposedly legitimate reason. In many cases, the links or attachments in the hijacked template are replaced with content made by the attacker, or malware is added. This type of attack is closely related to spear phishing in that it specifically targets certain individuals or organisations.
An example of email clone phishing is an attack on customers of an online retailer. The attacker clones the merchant’s email template and changes the link that is supposed to take the recipient to the merchant’s payment page. The link instead takes the recipient to a fake page where the attacker can steal the victim’s payment details.
The risk for victims is that they reveal sensitive information that can be used by the attackers for financial fraud or identity theft. The emails used by the attackers can look deceptively genuine and come from legitimate businesses or organisations, so victims can unwittingly give sensitive information to the attackers.
Protection options and preventive measures against vishing
- Verify the sender’s email address to make sure it originates from a trusted source.
- Carefully check the content of the email, especially links or attachments, before clicking on or downloading them.
- Use unique and strong passwords and enable two-factor authentication wherever possible.
If you are worried whether your data has been stolen, then you can use the Identity Leak Checker from the University of Bonn.
Identeco offers suitable products for the protection of employee as well as customer accounts: Identeco: Our Products.


Artikel teilen