Protecting Your Data from Ransomware Attacks: How to Secure Yourself and Your Business
- Reading time:
- 3 min

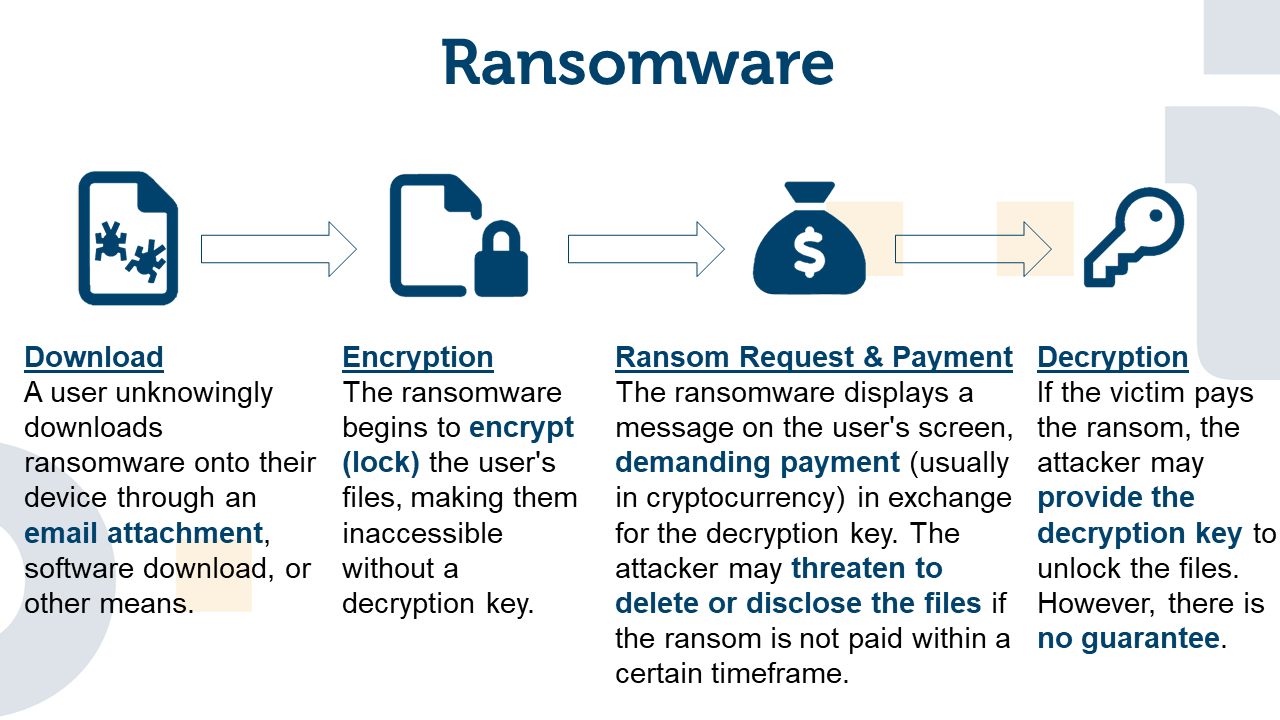
Ransomware attacks are one of the most dangerous threats in cyberspace. They enable attackers to access and encrypt important data and systems of companies and private individuals. The attacker then usually demands a ransom to release the data. Some variants additionally specifically encrypt backups and copies, so that a ransom payment seems inevitable.
Users risk losing important data and files if the ransom is not paid. There may also be financial losses, as many attackers demand the ransom in cryptocurrencies, which are also difficult for law enforcement agencies to trace.
For affected companies, a ransomware attack can lead to considerable economic damage, as business processes are interrupted and important data can be lost. The company’s reputation can also be affected by an attack.
Once encryption is complete, a ransom is usually demanded by displaying a ransomware note as the desktop background. After paying the ransom, the victim is provided with a key and a program by the attackers to decrypt the encrypted files.
Example 1: WannaCry
A well-known example of a ransomware attack is the WannaCry virus, which made headlines around the world in May 2017. The attack had a huge impact on businesses and organisations in several countries, including hospitals in the UK, which were forced to activate contingency plans and divert patients to other hospitals.
Example 2: Colonial Pipeline
Another well-known example is the attack on the US oil and gas utility Colonial Pipeline in May 2021. The attack resulted in the need to halt the pipeline’s operations and caused shortages in gasoline deliveries to gas stations on the east coast of the US.
Example 2: JBS
Another example is the attack on US-based JBS, one of the world’s largest meat suppliers in May 2021. The attack impacted JBS operations in North America and Australia, and the company had to temporarily close some operations.
It is important to be aware that ransomware attacks are a growing problem and to take appropriate protective measures to protect yourself and your business from attack.
Protective measures against ransomware
- Back up important data and files regularly to have a backup copy available in case of an attack. It is important to store them on a separate, secure device or platform that is not connected to the network. We describe such an approach in one of our other blog posts: A Ransomware Secure Backup Strategy.
- Ensure that regular checks are made to see if it is possible to restore data from the backup.
- Keep your software and operating systems up to date to close security gaps.
- Use a firewall and anti-virus software to block unwanted connections as well as known threats at an early stage.
- Be wary of emails from unknown senders and avoid opening attachments to emails that appear suspicious.
- Be especially careful when visiting websites you do not trust and avoid clicking on links in emails and messages you were not expecting.
- Train your staff regularly on how to deal with emails, links and attachments from unknown sources.
- Access restrictions: Limit access to sensitive data and systems to only necessary people. Limit the administrator rights of users to prevent the execution of malicious software.
- emergency and recovery plan: Create emergency plans to act quickly in the event of an attack and minimise the impact.
- Secure their access to corporate resources, both internal and external, from credential stuffing and account takeover attacks. Ensure that no username and password combinations are leaked and can be used by attackers.
In 2020, there was a significant surge in these attacks, mainly due to the sudden shift to remote work for many companies. The majority of organizations were ill-prepared for this IT landscape transformation. Notably, attacks on critical infrastructure such as hospitals created widespread concern.

Artikel teilen