Phishing #5: Malvertising, Https-Phishing und Evil Twin
- Reading time:
- 6 min

Malvertising
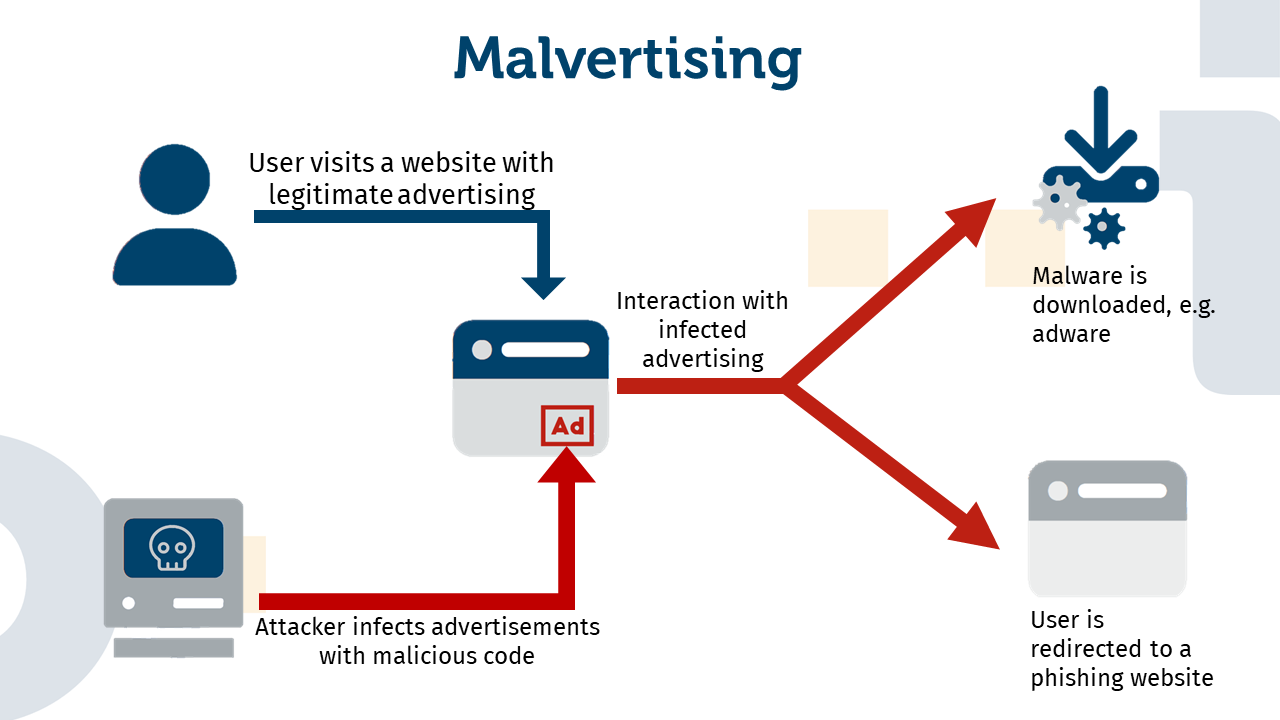
The term “malvertising” is composed of the words “malicious” and “advertisement” and describes an attack in which malicious code is embedded in online advertisements in order to carry out harmful activities on the user’s computer or device. Often, the victim is redirected to a phishing site without being noticed. But how can this happen if the advertising itself is harmless? This has to do with the complicated structure of online advertising. Although an advertisement actually promotes a specific company, it is produced and published by another company. Often, however, the advertisement is published on several domains, so that the user has to be redirected several times after clicking on it. Attackers exploit these many redirects to infect the advertisement in places where it is unlikely to be noticed.
When a user is attacked by malvertising, there are essentially two possible scenarios: In either case, the user is redirected and ends up on a phishing page. This situation then resembles a pharming attack. The other scenario is that malware is downloaded onto the user’s computer. This can be all kinds of malware, from ransomware to adware.
Adware is itself a compound word and consists of “advertising” and “software”. Unlike malware, adware is not necessarily malicious by itself. Its purpose is, among other things, to display advertisements to generate revenue for developers. However, adware can often be perceived as unwanted or annoying by users, as it often displays excessive advertising or interferes with the normal use of the computer. Some adware also collects information about users’ surfing behaviour without their explicit consent. In this case, the software can be clearly classified as spyware and thus as malware.
How to protect yourself from malvertising:
Antivirus software: Antivirus software helps prevent malware from downloading.
Ad Blocker: The most effective tool against malvertising is an ad-blocker, as it blocks all types of online advertising and thus also corrupted ads.
Always update browsers and additional programmes: This measure is most likely to help against malvertising, which starts without interaction with the advertisement.
HTTPS-Phishing
HTTPS is nowadays associated with security. This is understandable insofar as the S stands indeed for “Secure”. HTTPS is thus the advancement of the HTTP protocol, which is used for the transmission of data between web browsers and websites. In order to make the data transfer more secure, the data is encrypted before it is transmitted, which is supposed to guarantee that only the website operator and the user can access the data. This means that an HTTPS phishing attack describes that the attacker also reads the data? As mentioned, this is exactly what is prevented by the HTTPS protocol. However, HTTPS phishing exploits precisely the security established by the protocol.
To use an HTTPS protocol, a certificate is required. This is easy to obtain, and attackers can use it to create their own sites using HTTPS. The user’s browser considers the attacker’s website to be legitimate and allows the user to access it. The attacker in turn makes his website look like a real login page, whether it’s from Outlook, Amazon or other big companies. If the user does not pay attention to the URL, he does not realise that it is a fake site and, in the worst case, enters his login data. The attacker can then use the given login data to gain access to the user’s account. If the attacker has taken over such an account, this is actually called an Account-Takeover.
How to protect yourself from HTTPS phishing:
Check the URL: Even if the page appears to be secure in your browser, it doesn’t necessarily mean that it’s the real deal.
Watch out if the appearance of the website has changed: Even if attackers imitate the real website, they may not copy everything correctly. This can be recognised by spelling mistakes or different colour tones.
Use multi-factor authentication (MFA): Even if an attacker got hold of your credentials already, you will be notified when they try to log into your account. If you use MFA, the attacker needs a one-time password (OTP) or something similar to log in. So if you receive an OTP without having logged in, you can react to it and change your password directly. You can also be sure that the attacker could not access your account.
Check your credentials: You should also regularly check that your access data has not yet been stolen. To do this, you can use the Leak Checker of the University of Bonn, for example.
Evil Twin
With this type of phishing attack, it is extremely easy for users to fall into the attacker’s trap. The evil twin is a malicious Wi-Fi network of the attacker, but designed to look like a legitimate Wi-Fi network. Such attacks are designed to take place in public spaces, e.g. in cafés or retail stores, anywhere customers want to access the Internet quickly. The attacker creates a hotspot with the same name and possibly also the same password as the Wi-Fi of the café in which he is currently sitting. The café customer’s device e.g. mobile phone tries to log into the café’s network, but first encounters the evil twin network and logs in there. In order to ensure that the customer’s end device chooses the evil twin rather than the original network the attacker often offers a stronger Wi-Fi signal than the original network. This takes advantage of the fact that end devices will always choose the stronger signal when they are presented with multiple signals with the same name and configuration.
If the user’s device has logged in, the attacker can monitor the user’s entire data exchange. Thus, an Evil Twin attack is often also the first step for a machine/man-in-the-middle attack. The attacker places himself between the user and the visited website and reads along. In the worst case scenario, the attacker may also steal some of the user’s account credentials.
How to protect yourself from an Evil Twin attack:
Avoid public Wi-Fi networks: If you do not use them, such an attack cannot happen at all.
Use VPN: These days, most consumers use mobile data, so they no longer need the benefit of public Wi-Fi networks. If you still want to connect to a public Wi-Fi network, you may want to consider using a VPN. A VPN provides a secure connection between your device and the Internet, so an Evil Twin attacker should not be able to read it.
Avoid critical interactions: If you are using a public Wi-Fi network, it is best to avoid critical account logins, such as online banking. This will prevent an attacker from capturing your credentials in the first place.


Artikel teilen