Phishing #7: Social Engineering
- Reading time:
- 5 min

To make phishing work, attackers rely heavily on “social engineering”. Social engineering refers to strategies used to persuade people to behave in a certain way. In email phishing, for example, the attacker makes the email look like an authentic email and phrases it with some urgency, such as informing the victim that their account is about to be blocked, which can only be prevented by clicking on a provided link. The goal is to get the victim to click on the link, where they are asked to enter passwords, for example.
But social engineering is not limited to digital attacks. Examples of social engineering in the analog world include “tailgaiting” and “USB phishing”. In this blog, we will look at these examples of social engineering and how you can protect yourself against them.
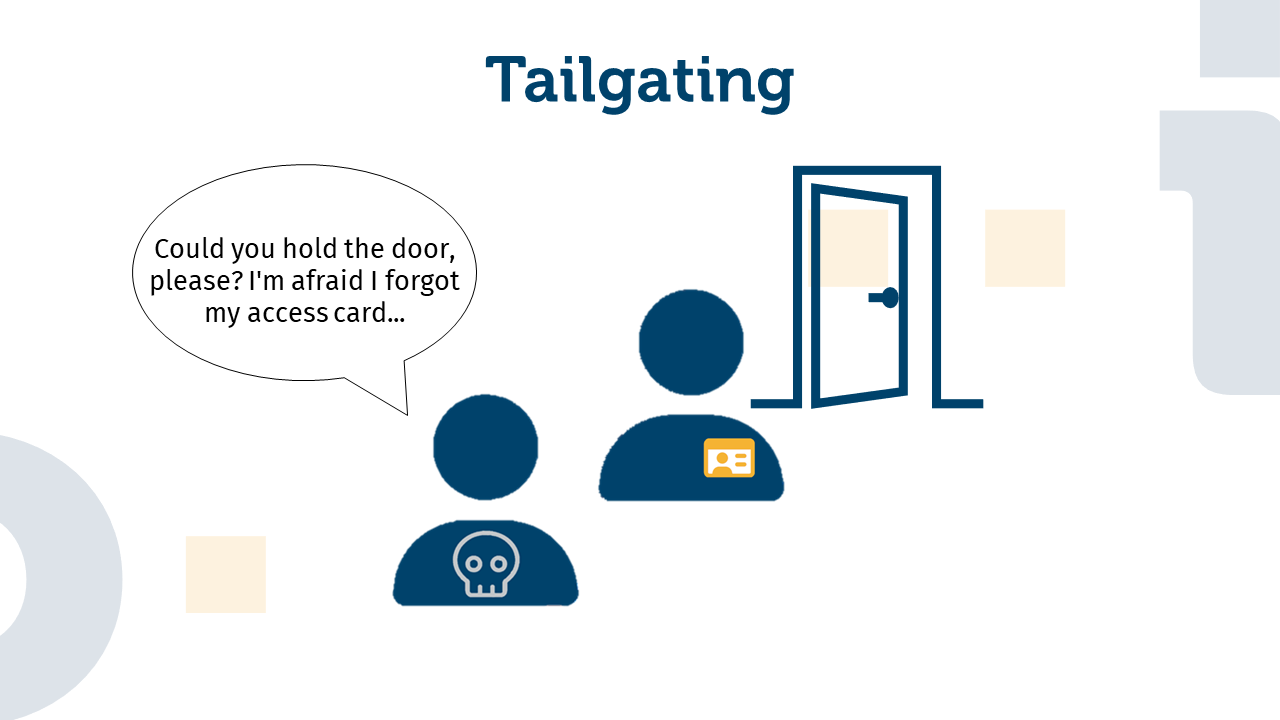
Tailgating
It is not uncommon to hold a door open for someone behind you. But within a corporate environment, this can be dangerous. Attackers sneak into buildings by pretending to have an appointment with someone, wanting to deliver something, or being unable to open the door themselves because they have forgotten their access badge. This method is known in the security context as “tailgating”.
This allows attackers to enter the building and cause damage in a variety of ways. They can steal, manipulate, or plant information. Sometimes, using the same or similar tactics, they are able to penetrate further, even into rooms containing sensitive information.
The word “tailgating” actually comes from tailgating in traffic (driving up to the tailgate). It was then imported into the safety context, with the meaning that when you tailgate in this way, you are also “following too closely”. Tailgating is also a type of party that takes place in the parking lots before major sporting events in North America. The name comes from the fact that people gather behind the cars, where drinks and barbecue are available directly from the open tailgates. However, this rather social event has nothing to do with the attack of the same name.
Piggybacking vs Tailgating
Piggybacking is not related to phishing or social engineering. However, this attack is so similar to tailgating that they are often confused or even used synonymously, which is why we want to mention it here.
Unlike tailgating, piggybacking involves the attacker being let in directly by an authenticated person who is intentionally in complicity with the attacker. The attack itself is therefore not directly based on social engineering. However, it is important to emphasize the difference. Piggybacking is planned with knowledge from within the organization, whereas in tailgating the attacker’s knowledge is more limited.
Tailgating und Piggybacking verhindern
Secure entrances: If an entrance is constantly open, anyone, including an attacker, can get into the building unnoticed. In such cases, you can often quickly remedy the situation yourself by closing or reporting the entrance in question. As a rule, the responsible security team should also be informed of such acute security problems.
Watch out for people: If a person looks lost, they may be approached for help. In most cases, this will not be an attacker. However, it is best to politely direct the person to the reception area or even escort them there.
Report suspicious persons: If a person looks suspicious in any way, a security guard should be notified. This also applies if a person is too close to a restricted area.
Implement and follow security protocols: A company protocol outlines how one should behave in certain situations. This includes how to deal with unauthorized persons.
USB-Phishing
USB phishing is a type of baiting where the physical USB flash drive is the bait. This attack takes advantage of the victim’s curiosity. The attacker leaves a USB flash drive somewhere where a victim can easily find it. Curiosity is piqued and the victim wants to know what is on the stick. To find out, however, the stick must be inserted into a computer. Once the USB stick is inserted, malware is downloaded in the background. Often a few files or photos are placed on the USB stick to distract the victim until the download is complete.
USB-Phishing verhindern
Do not use found USB sticks: No matter where you find a USB flash drive, never plug it into your computer.
Turn off autorun: When you plug a USB flash drive, previously also CD or DVD, into your computer, it is automatically opened or its contents are executed. Disabling autorun stops this from happening, which can prevent malware from being downloaded.
Return found sticks to lost-and-found: If a USB drive has just been lost, it is best to take it directly to a lost-and-found location. That way, the owner can pick it up and there is no risk of other people interacting with the USB and possibly picking up malware.
Conclusion
At first glance, tailgating and USB phishing seem to have little to do with each other. But tailgating, like every phishing attack, is also based on social engineering. Specifically, tailgating exploits the politeness of employees, while USB phishing exploits their curiosity.
In contrast to tailgating, phishing attacks aim to steal sensitive data - often access data. This access data can then be used to penetrate accounts or take over accounts. This is then a case of digital identity theft.
Identeco specializes in the automated prevention of digital identity theft and account takeovers. If you want to know exactly how this works, write us an email or get in touch with us via our contact form.


Artikel teilen