Phishing #6: Spearphishing, Watering-Hole Attack and Whaling Attacks
- Reading time:
- 5 min

Spearphishing Attack
Spearphishing is a form of phishing attack in which specific victims are selected. In most cases, these are individuals, but it can also happen that a group, e.g. within an organization, is targeted. This type of phishing is very dangerous, as the attacker collects information about the victim over a longer period of time in order to create a personal dossier. The messages to the victim are then personalized in such a way that their trustworthiness is not questioned. This can lead to malicious links being clicked, malicious attachments being opened or sensitive information being passed on.
Recognize spearphishing attack
- Unknown sender address: You should always be skeptical of an unknown sender.
- Unexpected message: Be extra careful if you receive unexpected emails from colleagues or superiors, especially if you are asked for sensitive information or asked for payments or other approvals.
- Unexpected contact channel: Even if you are approached via an otherwise unusual contact channel, you should be particularly skeptical. If your company generally communicates via email and Microsoft Teams, but you are contacted via WhatsApp or SMS, this may also be an indication of an attacker.
- Spelling: If an email or other message seems suspicious, you can also look out for other signs of a phishing attack, such as grammatical and spelling mistakes. You can find out more about this in our first Phishing blog post.
- General caution: Even if you cannot identify any direct signs of a phishing message, you should be cautious about opening links or files, especially with external messages.
- Second Channel: If you are still in doubt, contact the supposed sender through an established channel, such as by phone. It is important that you make contact to obtain confirmation and not, for example, use an incoming call for this purpose.
- Minimizing the digital footprint: As mentioned at the beginning, an attacker needs as much information as possible about their potential victim. Therefore, keep your digital footprint in social media and other publicly accessible sources as small as possible.
Watering Hole Attack
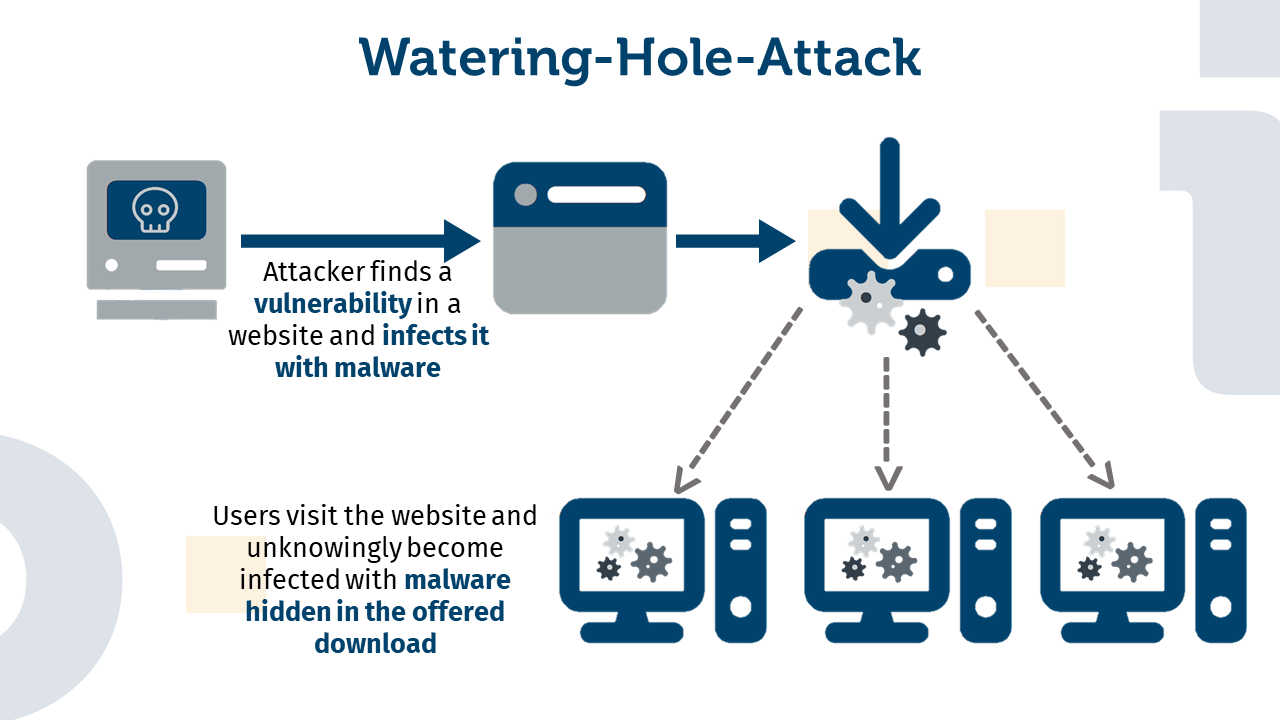
The tactic known from nature of hunting prey at watering holes is used in a very similar way in this phishing attack. However, here the attacker does not attack individual victims directly, but a shared resource, for example the download page of software offered free of charge. By exploiting a security vulnerability, the attacker can succeed in injecting malware into the download. Visitors then install malware unnoticed when they download the free software.
Recognizing a watering hole attack
- Unusual activity: If your device shows unusual activity after visiting a website, this may be a warning sign of such an attack.
- Official sources: Obtain software from official sources and be skeptical if the price differs significantly from the market price or if paid software is offered for free download.
- Antivirus software: Take the security warnings of your antivirus software seriously and keep it up to date to detect potentially dangerous downloads at an early stage.
- Phishing emails: Depending on how much access an attacker has to a website, they may be able to create their own subpages or emails for a newsletter. In this case, look out for clues such as grammatical and spelling errors. You can find more information in our first Phishing blog post.
- Check certificates: Especially for download offers, the website and the software should be digitally signed, i.e. have a certificate. This serves to prove the authenticity of the website or software. Download offers without a signature and therefore without a certificate should be met with particular skepticism.
Whaling Attack
We have already reported on CEO fraud and corporate phishing in this blog series. However, in a whaling attack, which is made up of the words “whale” and “phishing”, the target is not ordinary employees but high-ranking individuals. The attacker poses as a trustworthy contact or business partner and attempts to steal sensitive information, initiate bank transfers or generally cause damage, for example to reputation. Of course, this also means that the attacker must be well informed about the target person in advance in order to be able to carry out this type of personalized attack at all.
Recognize whaling attack
- Unusual requests: Always be suspicious of unexpected requests. Especially if large sums of money or confidential information are requested.
- Second channel: If you have any doubts, contact the alleged contact through an established channel, e.g. by telephone. It is important that you make contact to obtain confirmation and not, for example, use an incoming call for this purpose.
- Phishing message: Depending on the research efforts of the attacker, some information may be incomplete or even incorrect, this can be a clear indication of a fraudulent request. Also look out for other characteristics of a phishing attempt, such as grammatical and spelling errors. You can find out more about this in our first Phishing blog post.
- Check the domain: Check the email domain to make sure it matches the actual organization. Pay particular attention to typos or mixing up numbers with letters in the domain address.
- Minimizing the digital footprint: As mentioned at the beginning, an attacker needs as much information as possible about their potential victim. Therefore, keep your digital footprint in social media and other publicly accessible sources as small as possible.


Artikel teilen