Phishing #4: Pharming Attack, Browser in browser Attacks and Doc Clouding Attacks
- Reading time:
- 5 min

Hardly anyone who uses the Internet today has not received a phishing e-mail. Often it is already recognisable from the appearance, the content or the sender that the e-mail is not genuine. Attackers also fake websites. In this part of our phishing series, we explain pharming, browser in the browser and doc clouding.
Pharming Attack
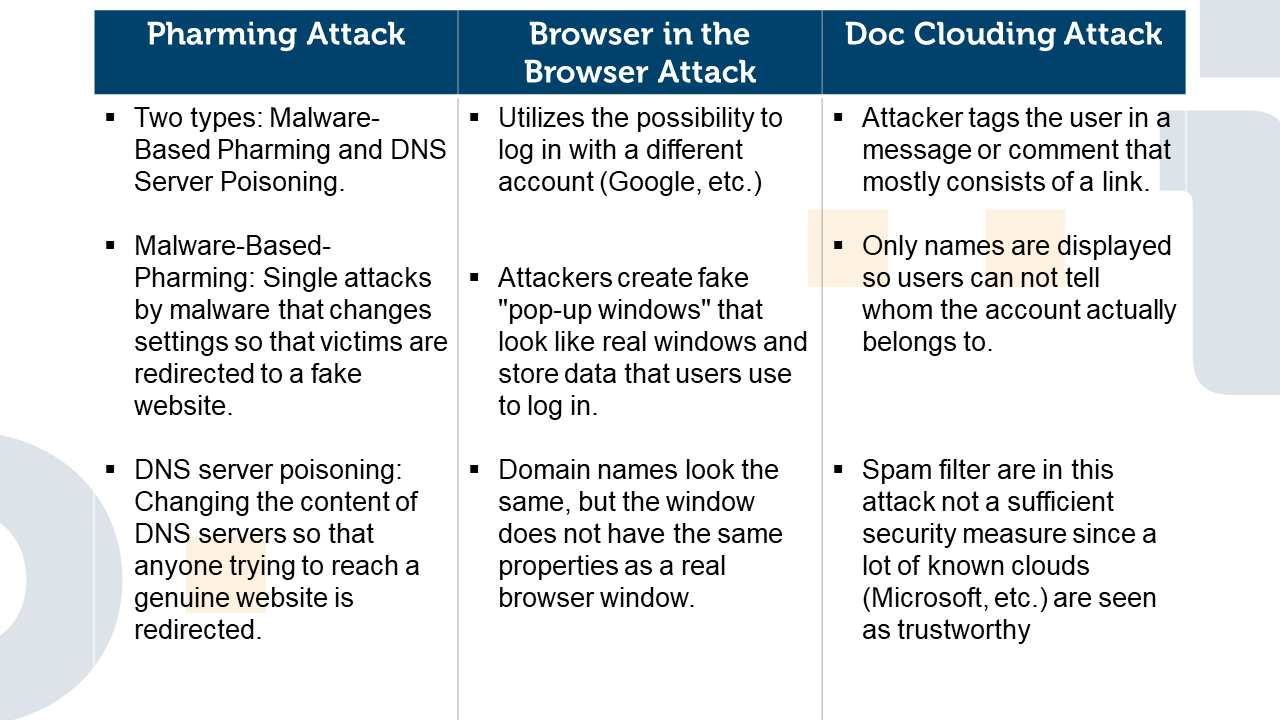
In this attack, the attacker tries to redirect the victim from the desired website to a fake website. There are two ways in which such an attack can be carried out. In malware-based pharming, the victim is attacked individually, this can also be accomplished via an infected email or another type of malware. The victim receives an email that contains malicious code, this code can change certain settings of the computer. If the victim wants to visit a website, he or she is redirected to the attacker’s fake site, even if the correct address was entered by the victim. The reason for this is that the redirection only takes place when an attempt is made to establish a connection. In most cases, the fake website looks exactly like the real one. DNS server poisoning is much more elaborate for the attacker, but also more dangerous for the user. DNS stands for “Domain Name System”. A DNS server has the task of converting IP addresses of websites into names and vice versa. In this attack, the attacker changes the content of the DNS server in such a way that users are directed to his fake websites, where not only data such as passwords can be stolen, but possibly also malware is distributed.
Detect Pharming Attack
- Incorrectly spelled domain names: An attacker will not be able to use exactly the same name for his fake site as for the real one. Therefore, you should make sure that everything is spelled correctly. For example, a “u” can become a “v” or a “p” can become a “q” and vice versa.
- Insecure connection: Nowadays, “https” is the most common type of connection as it is more secure. If it is a fake website, security is not a priority and “http” is usually used.
- Changed design: Even small things like a different colour can indicate that a website is fake. In addition, the texts of the website may contain errors that are not only noticeable but also frequent.
Browser in Browser Attacks
Many users prefer to log in only once and then stay logged in when they visit a website. In addition, many websites allow users to log in using another account such as Google or Facebook. Attackers take advantage of this and create a “pop-up window” that resembles the real login window and is just an overlay on top of the actual website. Instead of just a login screen, this attack replicates the entire browser window, including the address bar, security lock and window title. If the login data are entered in this window, they are sent to the attacker, who then has access to the user’s account. In this case, it is also more difficult to distinguish the real site from the fake one, as the usual security parameters such as domain name and security lock are correctly displayed.
Detect Browser in Browser Attacks
- Resize: The fake login window cannot be resized or behaves abnormally.
- Moving the window: The pop-up window cannot be moved out of its “parent” window. A real window can be moved to any location.
Multi-factor authentication can also protect against browser-in-browser attacks. If you accidentally enter your credentials in a pop-up window, the attacker still can’t log into your account. Moreover, it is obvious to the victim that this login window is not real. This is because no SMS code is sent or a one-time password is not requested for authentication. If the user notices the attack after entering the password, he should still change his password so that the attacker no longer has any valid data.
Doc Clouding Attacks
With the transition to the home office at the beginning of the pandemic, the editing and sharing of files in the cloud has once again increased sharply. This also made attacks on this more and more interesting for attackers. In a doc cloud attack, the victim is notified, of a supposed tagging, a new upload of a file or a new comment in an online document. As part of the email, a link is often shared, which then leads to the download of malware. Automated protection against such an attack is difficult. Since the actual email is usually a legitimate notification email from the provider informing about a comment or a new file in the share. Furthermore, the acting user is usually only referenced by name, an assignment to employees of the own company or legitimate external parties is sometimes difficult.
Detecting Doc Clouding attacks
- Password protected: Password-protected archives bypass the cloud providers’ malware protection and should therefore be treated with extra caution.
- Lack of context: Unsolicited shares or comments and links in documents should raise scepticism and be treated with caution. These can also come from legitimate colleagues if their user accounts have been compromised.
- Unknown cloud storage: Non-corporate cloud storage is an indication of a possible attack and should be reported to the IT security team if necessary.
- Executable files: Executable files and programs are rarely distributed via cloud providers in a business context. Do not run any third-party programs from the internet or the cloud on your computer.
If you are worried that your personal data has been stolen, you can use the Identity Leak Checker of the University of Bonn.
Identeco offers suitable products for the protection of employee and customer accounts: Identeco: Our Products.


Artikel teilen