A Pentest for Identeco
- Reading time:
- 4 min

On behalf of one of our long-standing partners, the IT consulting company Cure53 carried out a penetration test of the Identeco solutions and a code audit of the cryptographic methods used by Identeco. Overall, Cure53 was very satisfied with the integration and security of the Identeco solutions. We would like to take this as an opportunity to talk about security tests, penetration tests and code audits.
What is a pentest?
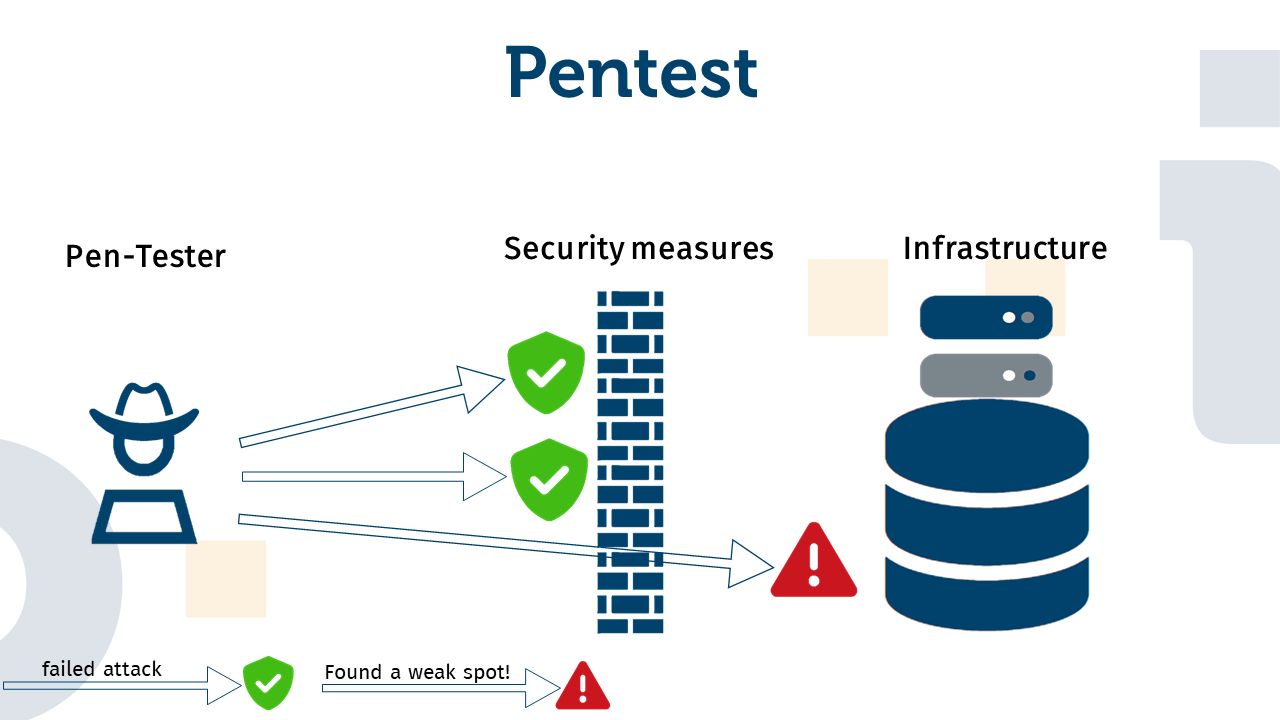
A penetration test (for short: pentest) is a security test from the perspective of an attacker. This means that the pentester assumes the role of a hacker in order to uncover vulnerabilities in the tested system. The aim is to find out how well a system is protected against external attackers. A pentest therefore serves to identify systemic vulnerabilities that would allow an attacker to penetrate the tested system, penetrate it to a particular extent or use it to an extent for which it is not intended. To represent a realistic scenario, the tester basically uses the same methods that a potential attacker would use to penetrate the respective infrastructure or manipulate the system. If a pentest actually identifies vulnerabilities that enable intrusion or manipulation, the operator of the infrastructure or system in question can react and close the relevant gaps, ideally before criminals exploit them.
For Germany, the Federal Office for Information Security (BSI - short for Bundesamt für Sicherheit in der Informationstechnik) has drawn up a guideline for carrying out penetration tests, which clarifies, among other things, the questions of how the pentest should be carried out, who should be involved, where it should be carried out, and what particular steps should be considered into account - from specifying the test object to the contract of the partners involved to the reporting phase. The BSI also recommends carrying out pentests on site, as experienced testers can develop a feeling for the weak points in the IT systems based on their impressions on site and discussions with those responsible. In Germany, the guideline for conducting pentests is actually legally relevant to the extent that certain institutions that are subject to “one of the protection goals of confidentiality, integrity or availability” must undergo a penetration test according to the specifications of the BSI (§).
To summarize, pentesting is a method of simulating attacks on a system to determine its vulnerabilities.
Code-Audit
A code audit involves manually checking the code for best practices, performance, bugs and security vulnerabilities. In this way, a code audit, like a pentest, also contributes to the security of the tested system. In contrast to a pentest, however, where the tested system is actually attacked dynamically, a code audit is more of a static procedure. In particular, unlike a pentest, the code must be visible to the tester.
Depending on what is to be tested, it makes sense to use different test methods. For example, a code audit can be used to check compliance with certain standards before a web application goes online, while a penetration test can uncover security vulnerabilities that are not directly visible from the code.
Pentest and Code Audit - A short summary
A penetration test, or pentest for short, simulates an attack on an IT system with the aim of identifying vulnerabilities in the tested system. A pentest is a common method for checking the security of IT systems.
In a code audit, a system or program is checked using its code. In contrast to a pentest, this type of test is static and the code must be visible
Our pentest
The IT consulting company Cure53 has performed a pentest of the integration of Identeco’s solutions into the infrastructure of one of our partners - with very good results. Cure53 decided to examine the implementation of the Identeco software in the respective infrastructure as well as the Identeco API for vulnerabilities and to subject the cryptographic procedures used by Identeco to ensure the anonymity of the exchanged data to a code audit.
The few - above all exclusively non-critical - findings were received by Identeco’s technicians as very helpful information and could be rectified in a very short time. In particular, the cryptographic procedures used by Identeco were emphasized and classified as very secure.
Conclusion
Penetration tests and code auditing are different methods of examining the security of IT infrastructures. In a penetration test, a tester attempts to penetrate the tested IT infrastructure using the same methods as a malicious attacker, while in a code audit, the tested system is examined manually and statically.
Why choose Identeco?
Identeco is not just a provider of high-quality security solutions, but a partner that works with you to develop the best protection measures in the context of corporate and platform accounts. Our customers value our expertise and commitment to their security. If you want to learn more about Identeco, don’t hesitate to contact us!
Artikel teilen