Man-in-the-Middle Attacks: How do you protect yourself from the invisible threat?
- Reading time:
- 5 min

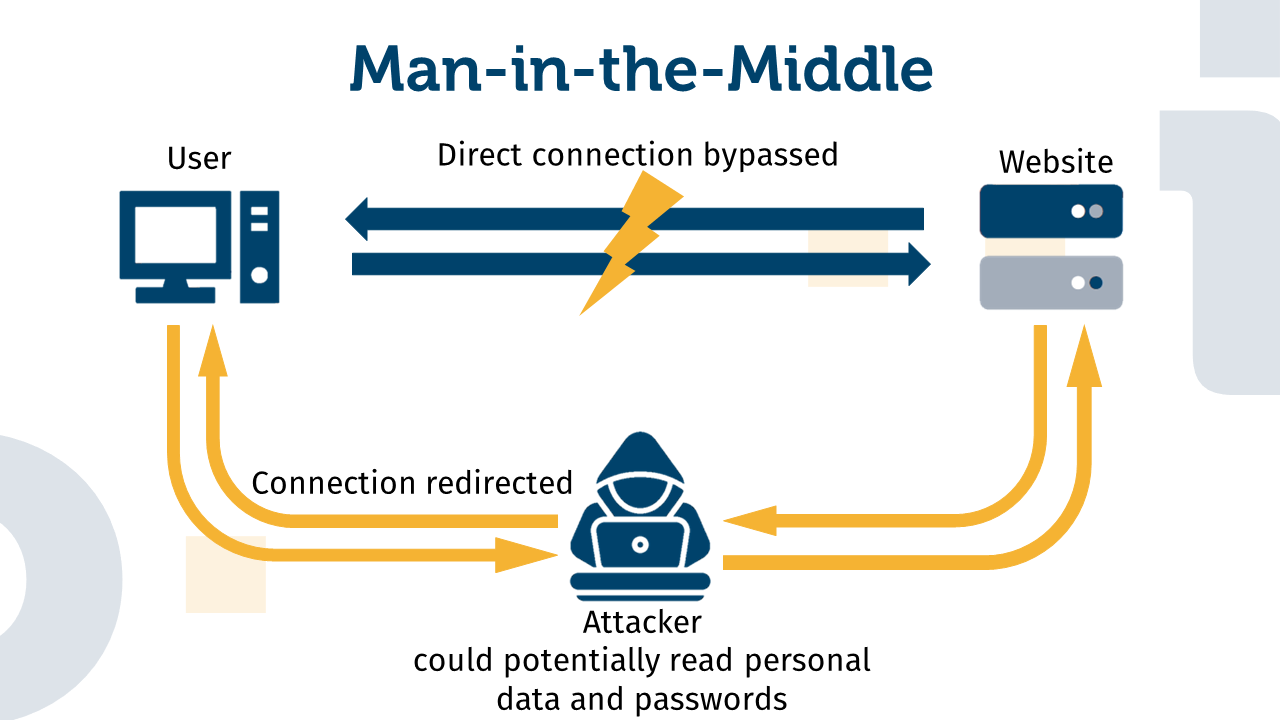
Man-in-the-middle attacks are a common method to steal information such as bank details or login information. In this type of attack, the attacker positions himself between the victim and the target to eavesdrop on or manipulate the communication between them.
How does a man-in-the-middle attack work?
To perform a man-in-the-middle attack, the attacker must trick the victim into connecting to a network he controls. This can be done, for example, by the attacker providing a public, unsecured Wi-Fi and naming the network so that it appears trustworthy. When the victim connects to this network, the attacker can intercept and manipulate communications between the victim and the target.
The attacker must make sure that neither the victim nor the target realizes that their connection is being manipulated. For example, the attacker can redirect the victim to a website he controls in order to use it to intercept personal data or even one-time passwords.
What is an example of a man-in-the-middle attack?
As an example of a man-in-the-middle attack, the victim may be sitting in a coffee shop and using a public Wi-Fi network named after the coffee shop. The attacker can control the Wi-Fi network by disclosing the network’s password and tricking the victim into connecting to the network. Once the victim is connected, the attacker can intercept and manipulate communications between the victim and the target.
Who carries out man-in-the-middle attacks?
The motivation behind a man-in-the-middle attack can vary. Some attackers want to steal personal information to gain financial benefits, such as access to bank account or credit card information. Other attackers may have political or ideological reasons and seek to manipulate or disrupt communications between two parties.
Man-in-the-middle attacks can also be carried out by state actors to gather information or disrupt secret communications between different parties. In any case, it is important to understand that these types of attacks should be taken seriously and that victims often do not even realize that their data has been compromised.
Therefore, it is important to be aware of these types of attacks and to make sure that you only access public Wi-Fi networks if they are trustworthy. To protect against man-in-the-middle attacks, using a virtual private network (VPN) can be a good option. A VPN encrypts the connection between the user’s device and the VPN server, protecting traffic from unauthorized access. For example, if a user is using an insecure Wi-Fi connection in a public area, a VPN can help prevent their data from being intercepted by attackers.
There are many paid and free VPN services available on the market. However, it is important to take time to compare the available options and make sure that you choose a service that is reliable and secure. It is also advisable to find out about the VPN provider’s data collection policy to make sure that the user’s privacy is not compromised.
Protective measures against MitM attacks:
Use of HTTPS websites: Users should ensure that they only access websites that use the HTTPS protocol. HTTPS ensures that the data exchanged between the user and the website is encrypted.
Use of VPN: A VPN can help encrypt the connection between the user’s device and the VPN server and protect traffic from unauthorized access.
Checking certificates: users should check the certificates of websites before logging into them or entering information. An invalid certificate may indicate that the user is on a fake website.
Use of antivirus software: Users should ensure that their antivirus software is up to date to protect against malware infections that can carry out man-in-the-middle attacks.
Avoiding public Wi-Fi: Users should avoid public Wi-Fi networks if they need to access them. If that’s not possible, they should at least connect to a VPN network to secure their connection.
Regularly review account activity: Users should regularly check their account activity to detect suspicious activity and contact the service provider immediately.
Enable two-factor authentication: Users should enable two-factor authentication wherever it is available. This ensures that an attacker who has access to the user’s password still cannot log in without also knowing the second factor of authentication.
Account takeover via Machine-in-the-Middle/Man-in-the-Middle attacks:
What is account takeover?: Account takeover is a type of identity theft. It occurs when an attacker gains access to a user’s account and is able to use it for his or her own purposes. Stealing or spying on credentials can be done in a number of ways.
Mitm attacks and account takeover: A MitM attack can result in the attacker learning the user’s password and being able to gain access to the user’s account in the future. This is done by redirecting the direct connection to the website through the attacker. This way, he is able to read the user’s login credentials and gain access to the account.
Moreover, it is possible to enter this password into a so-called dictionary. Such dictionary is a kind of list of possible passwords. It is mainly used in brute force attacks.
- How to protect yourself from account takeover: There are many ways to protect yourself from account takeover, even without installing additional software. You can avoid public networks and insecure websites, such as those that don’t have an HTTPS connection. Modern browsers will warn you when you try to visit an insecure website.
Moreover, it is always advisable to use at least two-factor authentication, as an attacker will not be able to gain access to an account even if he uses the correct credentials.
Regularly reviewing activity in your account will help you detect suspicious activity as early as possible. If you notice irregularities in your account activity, you can react quickly, for example, change your password.

Artikel teilen