Malware #1: Malware, Virus and Worm
- Reading time:
- 3 min

Malware
The word “malware” is a contraction of the words “malicious” and “software. Malware is software that has been developed to disrupt, burden and/or gain unauthorized access to systems, be they computers, networks or servers. The term is now used as a generic term for any type of malware. This includes “viruses”, “worms”, “Trojans” and many others.
Since the early 1970s, the development of various malware has continued to evolve, leading to the many subdivisions we know today. In the past, the motive was mostly just the will to do harm or even pure curiosity, but around the turn of the millennium it shifted to profit.
Virus
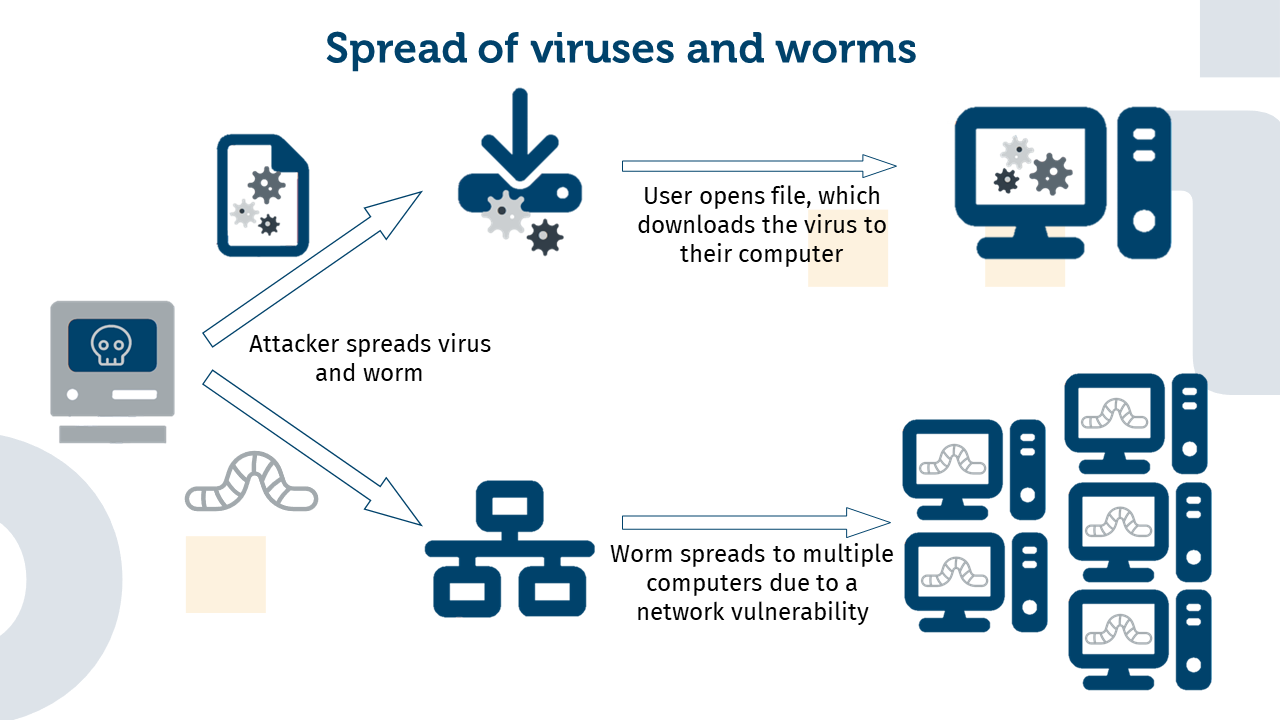
Viruses are a special type of malware. They can be compared to the pathogens of the same name since they spread from an infected computer to other computers. To do this, viruses need a host file or program into which they can integrate. Once activated, viruses can perform harmful activities, such as deleting files, slowing down the system or collecting personal data.
„ILOVEYOU“-Virus
- Spreading: This virus was spread via e-mail in May 2000. The subject line was “ILOVEYOU” and the attachment contained a file named “LOVE-LETTER-FOR-YOU.TXT.vbs”, which was intended to trick recipients into opening the file. In order to spread further, it replicates and sends more infected emails to the recipient’s contacts.
- Damage: Email servers were overloaded due to the rapid spread of the virus. Files on individual computers were replaced with copies of the virus. Additionally, passwords were sent to the perpetrators.
- Further consequences: Some companies had to shut down their email servers to prevent further spread. This caused them financial damage. Although the authors of the virus were found, they could not be convicted because there were no laws against the production and distribution of such malware in the Philippines, the country of origin of the virus, at that time.
Worms
Worms are another form of malware that can spread on their own, but without the need for a host file. They use networks and vulnerabilities to get from one computer to another. This makes them particularly dangerous, as they can spread quickly through networks. In this way, they slow down a network without being harmful themselves. However, this does not mean that they cannot transmit malware.
Blaster-Worm
- Spreading: This attack targets a vulnerability in Windows, also known as the “DCOM RPC” vulnerability. The worm was able to sneak in and replicate on machines running a specific version of the Windows software without requiring any action from the user. As a result, not only did it infect many computers, but it did so very quickly.
- Damage: Unlike most malware attacks, the hacker’s goal was not to steal personal data or money, but to exploit the vulnerability of Microsoft Windows, which is why the worm is also known as “MSBlaster”. The worm was programmed in such a way that at a certain point in time, all infected machines sent requests to a specific website, thus performing a “Distrubuted Denial of Service” attack (DDoS).
- Further consequences: In addition to the Internet disruption caused by the DDoS attack, this attack also demonstrated the importance of secure and updated software.


Artikel teilen