The Leak Inspector – Quick Email Checks for Data Breaches
- Reading time:
- 6 min

Easy Data Breach Checks – with the Identeco Leak Inspector
Data breaches happen every day – and often it goes unnoticed that your own email address is affected. In this article, we introduce our new tool for detecting leaks: the Leak Inspector. Learn how the Leak Inspector works, what makes it unique, and how you can use it to easily protect your digital identity.
- What Already Exists
- Why the Leak Inspector?
- What Data is Included?
- Why is the Check Worth It?
- It’s That Simple:)
- Try it Now – and Feel Safer
- The Leak Inspector for Businesses
- Still Have Questions?
What Already Exists
There are already some useful tools available for checking if your email address has been involved in a data breach, such as the Leak Checker from the University of Bonn. We have previously introduced the Leak Checker in our own blog article as a German alternative to “Have I Been Pwned.” The advantages of the Leak Checker over other tools (European data protection standards, password detection, number of records in the underlying dataset) have been discussed in detail in that article.
Why the Leak Inspector?
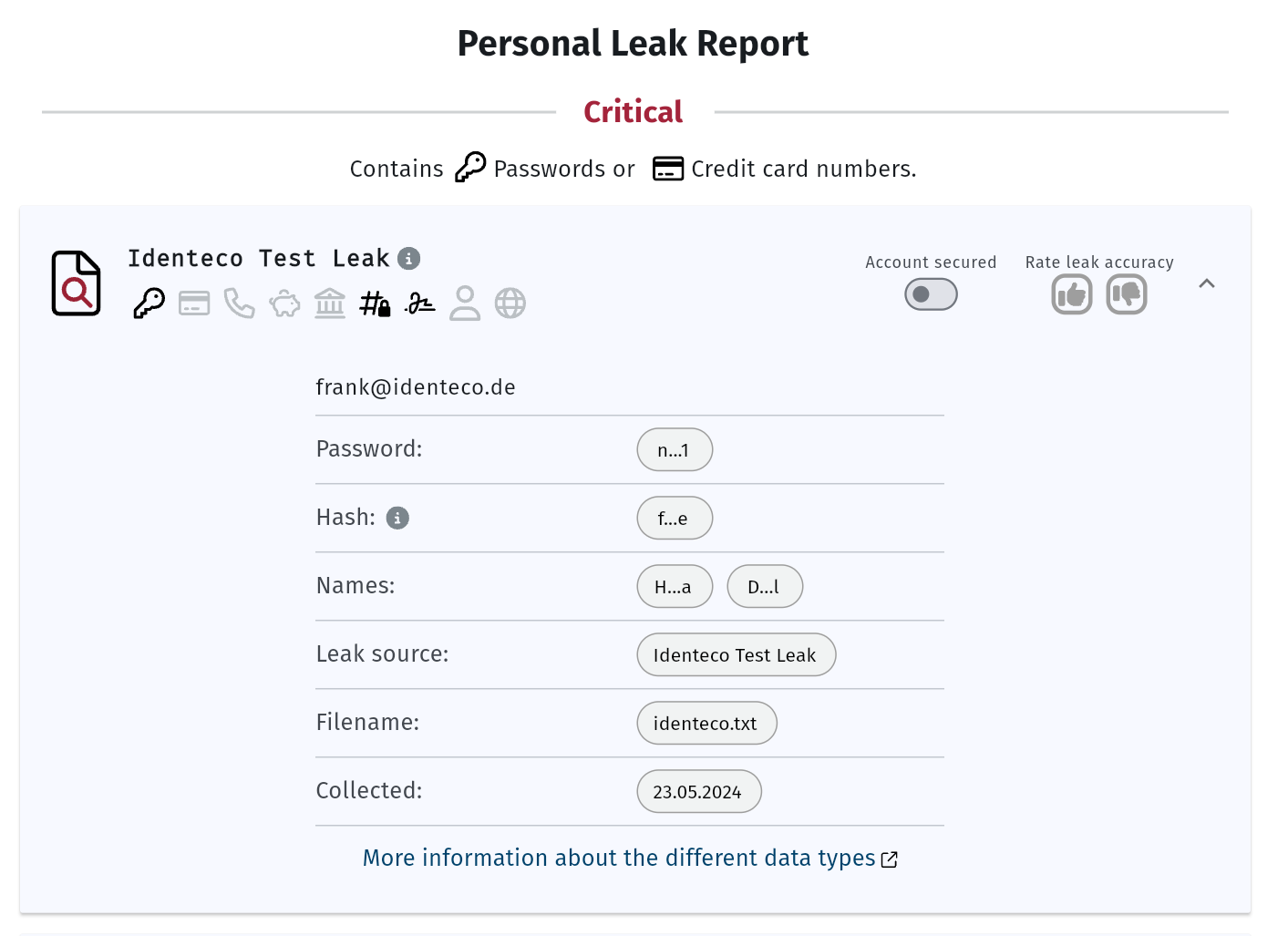
If there are already some decent tools for leak checks, why do we need the new Leak Inspector? The major value of the Leak Inspector lies in its interactivity, which manifests in several ways: the criticality assessment, the ability to mark a leak as processed, and the option to rate the leak’s accuracy.
Criticality Assessment – How Dangerous is a Leak?
The Leak Inspector categorizes leaked data into three criticality levels, so you can immediately see how serious the situation is:
Low means that “only” your email address is affected – a first warning that you should still keep an eye on. Such data is often used for generic phishing attempts or spam.
Medium indicates that additional personal data, such as your name, address, or phone number, has been leaked. A correct salutation and further details from the leak can make a message seem legitimate – potentially leading you to click on a harmful link or download. Stay especially vigilant when receiving suspicious emails that seem personally tailored to you.
High flags particularly critical leaks, such as plaintext passwords or hashes of your credentials. This requires immediate action: as soon as you recognize a password, change it everywhere you have used it.
This helps you quickly assess your check results and take appropriate protective measures.
Managing Leaks – Keep track
Most leak-check tools present a static list of leaks containing your email address. That’s useful for an initial overview. However, every time you check, you’ll often see the same, possibly outdated, information again.
The Leak Inspector solves this by allowing you to mark leaks as “processed.” Once you’ve taken action on a leak – such as changing a password – you can simply toggle the “Account secured” switch. The next time you use the Leak Inspector, that leak will appear grayed out and listed at the bottom of the page. This makes it easier to keep track of processed leaks and to spot new leaks faster so you can address them promptly.
Leak Validation – Is the Leak Actually Valid?
Besides marking leaks as processed for your own tracking, you can also provide feedback on the accuracy of the leaks. If the data in a leak is correct, you can confirm it with a “thumbs up.” If it’s not accurate, you can give a “thumbs down.” This feedback is invaluable for helping us better assess leaks and, for instance, evaluate their criticality.
The following image shows the three main features of the Leak Inspector: marking a leak as critical, rating a leak with a thumbs up or down, and using the “Account secured” switch to mark a leak as processed and accounts secured.
What Data is Included?
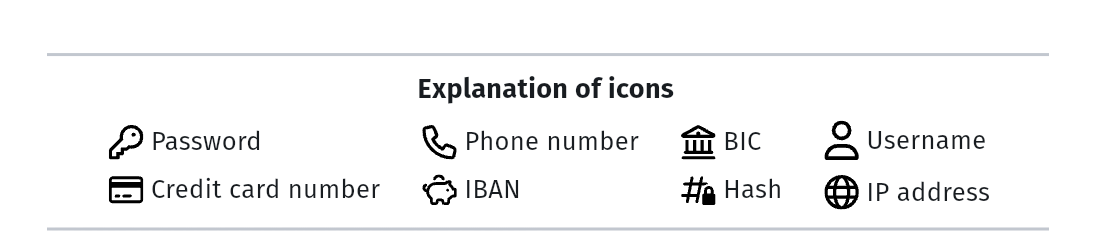
A data breach can include various types of information, such as passwords, IBANs, phone numbers, credit card numbers, and more. The Leak Inspector presents the data found in a leak in a clear, icon-based format. This allows you to quickly see which personal data has been compromised.
To ensure maximum data protection, sensitive details are partially masked with asterisks (as you can also see in the picture above). This keeps the specifics hidden from outsiders while still allowing users to identify the type of data that has been leaked.
Leak Inspector: Your Benefits
Criticality Assessment at a Glance: Instantly see whether it’s a harmless leak or a critical incident involving password exposure.
Document Processing Status: Mark leaks as Account secured to keep track of your security status.
Provide Feedback: Rate the quality of a leak with thumbs up or down to help improve the data quality.
Detailed Leak Information: Quickly understand which data is included in a leak – presented visually and with privacy in mind.
Why is the Check Worth It?
If your email address and passwords have been affected by a data breach, your accounts can be at risk. Our Leak Inspector helps you spot early warnings and take appropriate security measures. This might include changing passwords for affected accounts or adding a second factor to secure your accounts.
A compromised account can lead to a variety of – but always unpleasant – situations (we covered this in a blog article about the effects of account takeover). So it’s definitely worth preventing an account takeover – and that means regularly and proactively checking your email addresses.
It’s That Simple:
Despite its many features, the Leak Inspector is incredibly easy to use:
- Visit the Leak Inspector website
- Enter your email address in the form
- You’ll receive an email with a link – click the link in the email
- View your results, rate leaks, and secure your accounts!
The entire process is anonymous and free.
Try it Now – and Feel Safer
Use our Leak Inspector right here:
👉 Go to Leak Inspector
And if you like the tool: Feel free to recommend it!
The Leak Inspector for Businesses
Account and password security is a critical issue for businesses too. The Leak Inspector helps companies restore account security.
Account Security for Companies
The security of company accounts is a key concern for any organization. Phishing attacks or data breaches often lead to credentials falling into the wrong hands – giving cybercriminals access to your IT infrastructure.
How the Leak Inspector Helps
With our leak monitoring service, employees are proactively notified about data breaches. The Leak Inspector complements this by allowing employees to check and manage their own personal leaks. At the same time, the Leak Inspector can provide feedback to security teams as soon as a leak has been reviewed and processed. This way, control over affected accounts is maintained, and security can be quickly restored across the company.
Still Have Questions?
If you’d like to learn how to secure your business accounts as well, we’re happy to help. Just reach out via our contact form, book a meeting, or send us an email.
Artikel teilen