How often should you change your passwords?
- Reading time:
- 4 min

Always and nearly everywhere you are told how to choose a secure password: Upper and lower case letters, numbers and special characters, no variations of already existing passwords and in no case use a password more than once. After you have chosen your password appropriately, the only question that remains is: how often you should change your passwords.
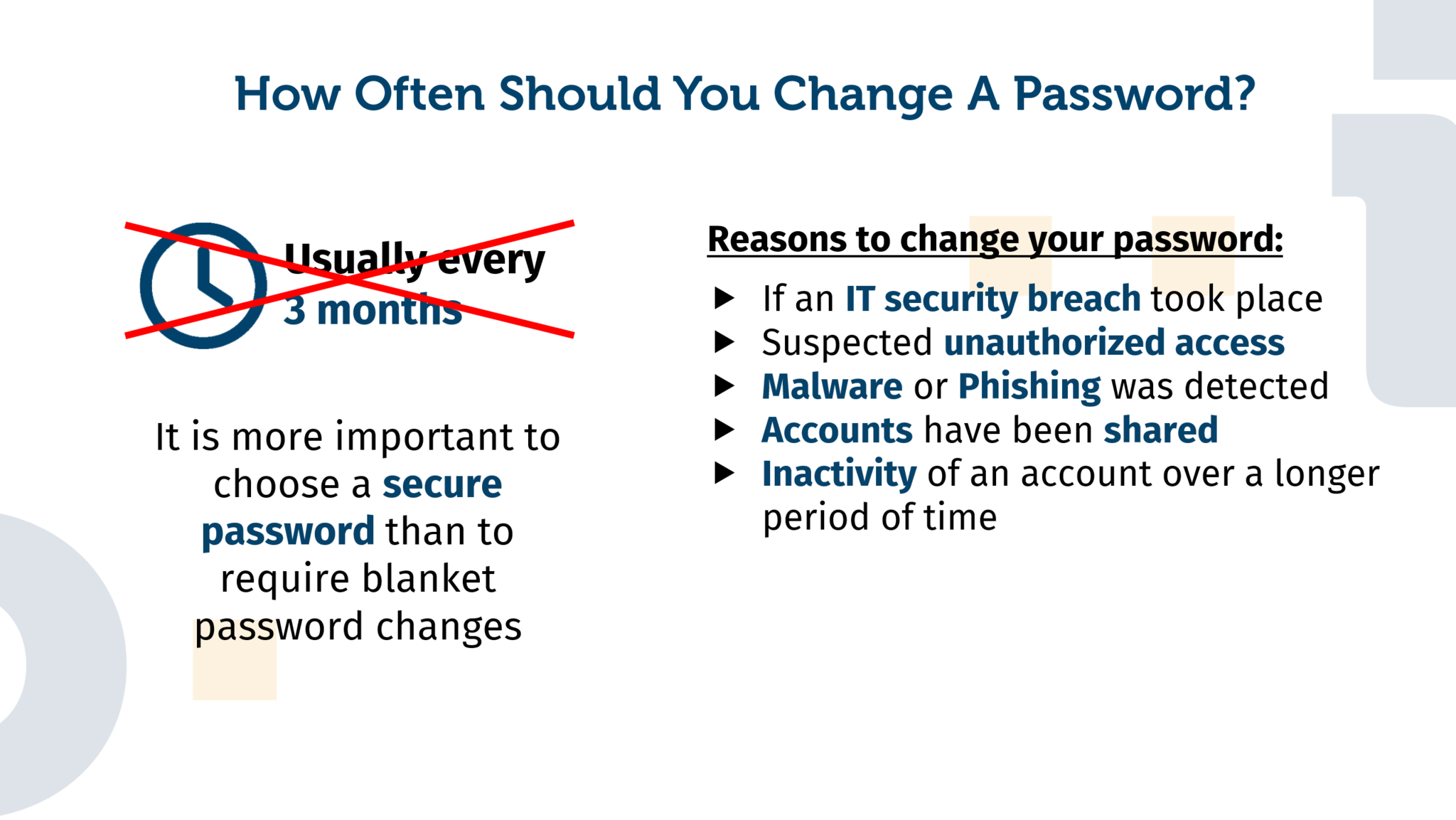
Originally, a regular password change several times a year was recommended, often every three months. At least that’s what experts thought for a while.
However, this changed and the common opinion now is to focus on changing a password rarely, it is rather emphasized to choose it correctly. Basically, it is advisable to use a password manager instead of remembering several long and different passwords. Regardless of whether they are employees, customers or even private individuals, many users state that they are overwhelmed with managing many different passwords. This inevitably leads to the choice of rather simple and thus insecure passwords, or to use the same password with slight variations, e.g. depending on the season, to add a certain number to the end. Unauthorized access to accounts with such passwords is often gained by attackers through pure guesswork or trial and error.
A long password that is as complex as possible, but especially unique, is the best way to protect an account, and the user should not be forced to change his password more frequently than once a year. However, this rough rule does not mean that you should never change a password, no matter how secure it is! In fact, there are some occasions when it is important to reset a password. Here are some of them:
If there has been a security breach in a company that manages your account, be it your own company or an external online portal. Then it can usually be assumed that your account has also been affected, and your own password should be changed directly. If you have used the password, even partially, for other accounts, the passwords for these accounts should also be changed.
If you suspect that someone has gained unauthorized access to an account, it is strongly advisable to change the corresponding password. For example, because someone was watching you closely when you entered your password, you had to use your password on a possibly untrustworthy device, or you observed suspicious activities or traces within your account.
Your password has been published in a data leak and is therefore no longer trustworthy at all. As a company, you can check this for your employees through our Identity Guard products.
No matter how careful you are there is no absolute security and malware or phishing emails can still get onto your computer or other devices in use such as smartphones. Also, if it happens that you are using a PC other than your own, it is important to log out of any accounts you may have used when you are finished. If you decide to pass on a device, for example to sell it, make sure that you have reset the device to its factory defaults and that all personal information has been deleted.
It’s very common to share an account with friends, usually involving the use of entertainment providers like Netflix or Amazon Prime. Often, after a longer period of time, you don’t know how many people actually share an account, which is why changing your password is important not only if, for example, your circle of friends changes.
It can also happen that you haven’t used an account for a while, but still don’t want to delete it. In this case, it is recommended to change the password from time to time, as you will not notice quickly if someone gains access to your account during the time you are inactive.
Additional protective measures can also significantly improve account security. Multi-factor authentication, for example, is a very effective protection approach. If a notification via push or SMS is used for this, you will also know if someone unauthorized tries to log into one of your accounts.


Artikel teilen