The Leak Checker of the University of Bonn: a German alternative to "Have I been pwned?"
- Reading time:
- 9 min
We are often asked how internet users can find out whether they are affected by data leaks. The name of the Australian/US service “Have I been pwned?” often comes up in this context and the question of a European or even a German alternative to “Have I been pwned?” arises just as frequently. In this blog post, we want to look into these questions: What is a leak checker, what is “Have I been pwned?”, what are German alternatives to it, and in particular, what is the University of Bonn’s leak checker?
New: The Leak Inspector
The Leak Inspector is a new interactive alternative to “Have I Been Pwned”. Find out more in our blog article.
Test now our new Leak Inspector!💡 The information in this article also applies to the Leak Inspector!
- What is a leak checker?
- Why do you need Leak Checker?
- What is “Have I been pwned?”?
- Alternatives to “Have I been pwned?”
- What should I do if I am affected by a leak?
- Leak monitoring for platform providers
What is a leak checker?
A leak checker is a service that can be used to determine whether your personal data is contained in a data leak. A leak checker is based on the amount of leak data available to it. This means that the leak checker compares the requested data with an existing database in order to determine whether it is contained. In particular, this means that the quality of a leak checker largely depends on the quality of the data it can use.
Why do you need Leak Checker?
When personal data is leaked, personal information such as email addresses, passwords, phone numbers or even credit card information can be compromised. This can quickly lead to identity theft, where criminals use someone else’s identity to carry out fraudulent activities. You should therefore regularly check whether your own data is included in a data leak and take timely measures to protect yourself, such as changing passwords. And the easiest way to check whether you have been affected by a data leak is to use a leak checker.
What is “Have I been pwned?”?
“Have I been Pwned?” is a leak checker operated by the Australian security expert Troy Hunt, which can be used to check whether you have been affected by data leaks. To do this, you enter the email address you want to check into an input mask and then receive information on whether and in which data leaks this email address appears.
What does “Have I been pwned?” mean?
The word ‘pwned’ itself is a made-up word from Leetspeak. “pwn” is derived from “own” by replacing the first letter with the letter “P”, which lies directly next to the letter “O” on the keyboard. “Pwn” thus means something like “defeat someone” or “dominate”. It can refer to other players in a computer game or to a computer system that has been hacked, i.e. “dominated”. “Have I been pwned?” therefore means something like “Have I been hacked?”.
Is “Have I been pwned?” trustworthy?
People often ask whether “Have I been pwned?” is reliable at all. In principle, “Have I been pwned?” is a reliable service, but it does not comply with current European data protection regulations. Beginning with the fact that any user is able to request and instantly receive information about any other email address. For example, a colleague’s email address can be checked to see if it is included in a leak, and if the leak belongs to a shady website or platform, it is possible to know more about the colleague than you should.
Alternatives to “Have I been pwned?”?
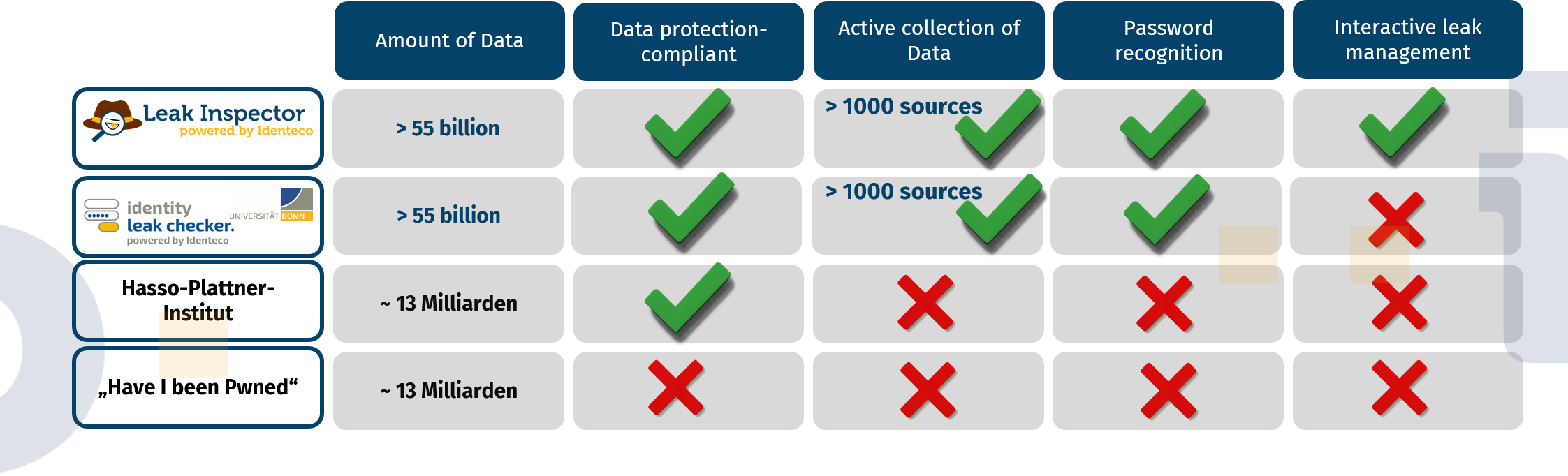
This leads to the question of alternatives to “Have I been pwned”, or perhaps even German alternatives to “Have I been pwned?”. Luckily, there are German alternatives available. Namely the Leak Checker provided by the University of Bonn and the Leak Checker from the Hasso-Plattner-Institute in Potsdam. So what is the difference between all these leak checkers?
The Database
A key quality feature of a leak checker is, of course, the database that the leak checker can access. “Have I been pwned?” and the Hasso-Plattner-Institute claims to have access to a database of almost 13-14 billion identities. The Leak Checker at the University of Bonn, on the other hand, has access to a database of more than 55 billion identities.
Up-to-date data?
“Have I been pwned?” and the Hasso-Plattner-Institute are mostly relying on data being delivered to them. The scientists at the University of Bonn, on the other hand, actively search the deep and dark web for leak data and can analyze around 300 million new data records every month, so that the leak checker of the University of Bonn can not only access a lot of data, but also very recent data.
GDPR compliance
As already mentioned, “Have I been pwned?” does not fulfil any European data protection guidelines. One of the reasons for this is that “Have I been pwned?” can be used to check basically any email address. The HPI and the Leak Checker of the University of Bonn solve this problem by sending an email to the submitted email address after the query so that no information about other people’s email addresses can be obtained. In addition, all data used by the Leak Checker at the University of Bonn is completely anonymized and encrypted and information about an email address can only be read if a request is made using this specific email address.
Recognizing passwords?
After an request has been made, both the Hasso Plattner Institute and the University of Bonn send an email to the email address provided. Similar to “Have I been pwned?”, the HPI and the University of Bonn also send information about the names of the leaks or files the data has been found in. At the University of Bonn, however, you also receive information about the first and last character of the leaked password. On the one hand, this information enables the receiver to recognise the leaked password itself, so that affected users can see whether the password is still up to date and is being used somewhere. On the other hand, this crumb of information is so limited that no one else can do anything with it if the email is intercepted or someone unauthorised has access to the email account.
More information?
Some data leaks contain other information, such as phone number, address or date of birth. At this point, however, the University of Bonn is explicitly focussing on email addresses and passwords, as this data is usually the most relevant for logging on to the Internet. In particular, the other services listed here only provide information about the fact, that a certain type of information is contained in a leak that looks similar to a phone number. Beyond that, however, you do not receive any information about the actual entry, such as the first and last character or the first two digits or similar. This may lead to greater uncertainty without any possible options to act. The University of Bonn’s Leak Checker focusses on the email address and password and avoids additional uncertainty.
Which leaks belong to which plattform?
An obvious question is, of course, which data leak actually affects someone. With “Have I been pwned?” and the Hasso-Plattner-Institute’s Leak Checker, you can find attributions to specific services. However, this should be treated with caution: All leak checkers use the same kind of data sources, primarily hackers who sell or share data on the net. The naming of the leak files generally does not follow a standardized or meaningful scheme, and is given by a criminal in the end. For example, if a file found is called “hr.txt”, it could be attributed to “Hessischer Rundfunk” (a German radio and tv station). However, the hr.txt file may actually have something to do with “Human Resources” or Hungary. Or it simply does not follow any scheme at all and was named automatically. And even if a standardized naming scheme were used: as the operator of a leak checker, you probably do not know this scheme and cannot trust criminals to have named their data accordingly. The University of Bonn therefore provides information about the names of the leak files that contain credentials, but does not attribute them to specific services or breaches. This is particularly important as incorrect attribution can lead to uncertainty among affected users.
Interim conclusion
We have discussed three leak checkers so far: “Have I been pwned?”, the Hasso-Plattner-Institute’s leak checker and the University of Bonn’s leak checker. “Have I been pwned?” does not fulfil the European data protection guidelines.The Leak Checker of the Hasso Plattner Institute and the Leak Checker of the University of Bonn both fulfil these data protection criteria in general, but the Leak Checker of the University of Bonn draws on a significantly larger database and provides a way of recognising passwords that have been used. Additionally, the Leak Checker at the University of Bonn does not attribute certain data leaks, partly because criminals are unreliable sources and partly because this avoids additional uncertainty.
What should I do if I am affected by a leak?
If you have concrete evidence or even just suspect that your data has been included in a data leak, it is advisable to keep calm and - if you have not already done so - check your emails with the University of Bonn’s Leak Checker. This will tell you whether and, if so, which passwords are stored in the data leaks.If you recognize the passwords, it is worth taking an inventory: have you used the password only once or several times and if so, with which services? It is then strongly recommended that you change the password for all services for which the password matches or comes into question, and ideally not to reuse any of the new passwords. The use of a password manager is recommended so that you don’t lose track of all the accounts.
Leak monitoring for platform providers
So far, we have mainly focussed on the available opportunities for consumers to determine whether they are affected by a data leak. However, platforms, online shops and companies also have the opportunity to protect their customers and employees accounts on their platform and inform them about data leaks if necessary. Identeco products can be used to automatically check employee and customer accounts on platforms for compromises. After all, not every end user is technically savvy enough to consider using a leak checker. This is where platforms and companies should use Identeco products to help their customers and employees in doing so and protect them from criminal account takeovers.
The Leak Checker of the University of Bonn is a cooperative project of the Department of Cybersecurity of the University of Bonn and the university spin-off Identeco. In particular, Identeco and the Leak Checker of the University of Bonn use the same database.
Test your accounts with our new Leak Inspector! Test your private accounts! Protect corporate accounts!
Artikel teilen