Effects of Account Takeover
- Reading time:
- 6 min

Consequences of Account Takeover
In our blog, we regularly report on the various technical ways to take over an account. An account takeover is the digital version of identity theft. In this process, criminals take over an online account, for example, through unauthorized authentication with hacked email and password combinations. In this article, we will take a somewhat non-technical look at account takeover and identity theft and shed some light on the possible consequences.
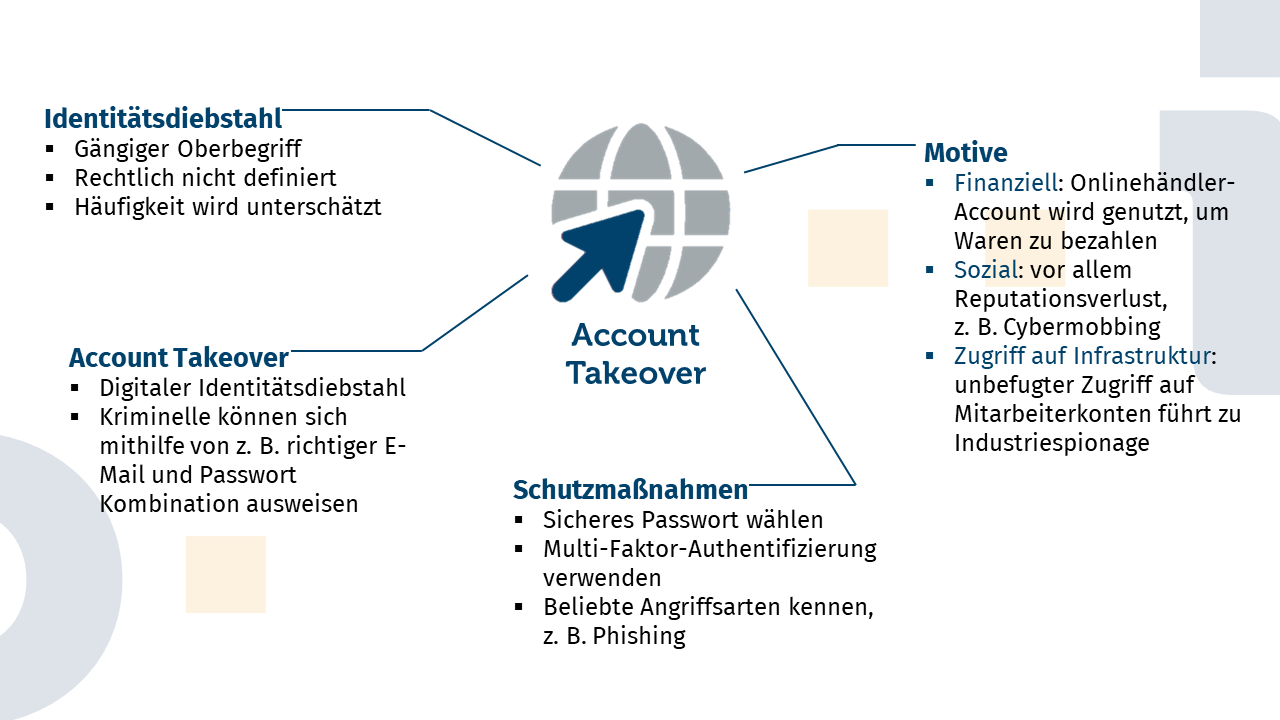
Identity Theft
Account takeover is a special form of identity theft. Although the term “identity theft” does not appear as such in the German Criminal Code, it is the common generic term for various comparable phenomena. These include “spying on personal data” (§202a) or “falsifying data relevant to evidence” (§269).
As mentioned above, the term “identity theft” is not defined by law. This is probably because identity theft cannot be theft at all due to the narrow legal definition of theft. A theft requires that the stolen property be a “movable thing,” and an identity is certainly not a thing. And whether it is movable or not seems to be a philosophical rather than a legal question.
Often, the first thoughts on the subject of identity theft are along the lines of “that can’t happen to me”. This is usually because people are not aware that anyone can be an attractive victim of identity theft. In fact, the phenomenon is not that rare. And in fact, our author has been a victim himself: When I was a teenager, I once lost my wallet, and shortly afterwards a cell phone bill fluttered into my house. A little later, I received a reminder from the debt collector Bonebreaker&Sons. Some contemporary who was not particularly well-disposed towards me had apparently found my wallet and used my ID and bank documents to conclude a cell phone contract. And that, cheekily, without my intervention. That was identity theft - in this case quite analogous.
The facts of the case were clarified and what remained was the memory of the uneasy feeling and a little story: After an initial fright, the requested contract and the poorly forged signature on it could be used to assure that I was not the specified contractual partner. This took the problem off the table for me. From a purely legal point of view, my case was simply a case of fraud, since an attempt was made to “obtain a pecuniary advantage by false pretenses” (§263).
Real World: Identity Theft – Virtual World: Account Takeover
An account takeover works much like the story above, only in the digital world. Criminals find something they can use to identify themselves digitally, such as a combination of email and password, and use that data to take over an account. All sorts of accounts can be taken over: Ebay, Instagram, Facebook, Twitter, the online points collection system of your favorite clothing store. Accordingly, taking over different types of accounts can have different implications. By the way, from a purely legal point of view, all these phenomena are at least “spying on data”, as it is the “unauthorized access to data […] by overcoming the access security” (§202a).
The Ebay account and my money
If an online merchant account is hijacked, the consequences are felt directly in the wallet: attackers quickly order masses of expensive products and often have them sent to a fake home address, often with the aim of reselling the goods. Before the victim knows it, the claims quickly add up to several thousand euros. The online retailers usually have to compensate for the damage and simply write off the loss, as in the case of shoplifting. At the same time, the losses are not insignificant. In 2020, the losses incurred by online retailers due to digital identity theft will amount to over one billion euros (€1,000,000,000)!
Twitter, Facebook and Co.
Social media accounts are less about money than about loss of reputation.
The schoolgirl whose Facebook page suddenly displays racist messages suffers the consequences in the schoolyard; the politician whose Twitter account advertises “Onlyfans” during the election campaign may miss out on a seat in parliament.
Account takeovers in social media are about bullying, disinformation and discrediting.
Especially if such a takeover is part of a general disinformation or bullying campaign, the consequences for those affected can be devastating.
Many identities - much theft
With the spread of the Internet, identity theft is becoming increasingly common. One reason for this is the new technical possibilities: Where once a wallet had to be found or identity documents had to be laboriously forged, criminals can now take over an account from their desks at home. On the other hand, it is also due to the multitude of digital “identities” we have acquired today. Most Internet users are registered with not just one, but rather five online merchants, plus numerous forums, social media, dating platforms, and so on. Yet security standards on the provider side and security awareness on the user side are not always very pronounced.
Makes it hard for them.
Criminals will always find security loopholes to penetrate somewhere without authorization, because no system is absolutely secure. But we can make their lives as difficult as possible. A start on the consumer side, for example, would be to be careful with data (that starts with not shouting company information into your cell phone on the train), to behave a bit more cautiously on the Internet, and to choose unique and complex passwords.
However, there are many other ways to protect yourself against digital identity theft. Basic technical options include multi-factor authentication, virus scanners, password managers, etc. In this blog, we always try to draw attention to such possibilities.
However, the platform operators also have options for protecting the accounts on their platforms against account takeover. One possibility is to use targeted leak monitoring to identify threatened accounts directly and to deny criminals access to such accounts.
Identeco offers ways in which platforms can protect their accounts from such attacks in a fully automated and data protection-compliant manner. If you would like to know how this works, please send us an email or get in touch with us via our contact form!
Conclusion
Identity theft is not a firmly defined term in legal terms, but a common generic term for various comparable phenomena such as “spying on personal data” or “falsifying data relevant to evidence.” Account takeover and identity theft, however, can have far-reaching consequences. The potential consequences range from financial loss and reputational damage to compromising a company’s entire IT infrastructure. Identity theft is unfortunately not uncommon and can hit you faster than you think. To make it as difficult as possible for criminals, responsible handling of personal data as well as strong passwords and caution in the digital space are necessary.


Artikel teilen