Understanding DoS, DDoS, and DRDoS Attacks: What Every Business Should Know
- Reading time:
- 7 min

When surfing the Internet, it happens again and again that a page loads very slowly or not at all. Many think that this is due to their Internet connection, but this is not always the case. If too many requests are made at once, it can happen that the servers are overloaded and only work very slowly. This is called “denial of service” or “DoS” in short.
In many cases, providers can anticipate that they will have to deal with more requests than normal. For example, if there are discounts or generally days when more shopping is done, such as on Black Friday or just before Christmas. If this is not the case, a DoS attack can be the cause and bring the website to a standstill for some time.
Classic DoS attacks
A DoS attack aims to make a resource, be it a website, server or network, inaccessible to legitimate users by overloading the capacity of the resource. This can be achieved through several methods, including:
Network congestion: an attacker sends a large amount of traffic to the target, exhausting the available bandwidth and blocking legitimate requests.
Software vulnerabilities: the attacker exploits vulnerabilities in the software or network protocol to crash the system or cause unexpected behavior.
Resource exhaustion: The attacker manipulates certain resources to cause their exhaustion. This can be done, for example, by creating infinite loops, overloading databases, or exploiting memory leaks.
An example to illustrate DoS attacks would be a person repeatedly flooding a website with a large number of requests. This overloads the website and makes it inaccessible to legitimate users. Modern websites can usually no longer be attacked by this type of flooding. However, if a software vulnerability becomes known, even a single manipluated data packet can be enough to successfully attack modern systems.
Technical background of DoS attacks
DoS attacks use vulnerabilities, exploits, or resource exhaustion to overload the target or make it unreachable. An attacker can use malicious software or trigger a DoS attack through local manipulations, hijacked user accounts, or misconfigurations in the system.
DoS attack vs. DDoS attack
In a DoS attack, the attacker usually uses only a single request or access opportunity. This attack is rarely seen in today’s world because redundant and more powerful systems and simple defensive measures prevent the attack or the impact is very low.
In contrast, one hears again and again about “DDoS” attacks, which stands for “Distributed Denial of Service”. This involves the use of a larger number of computers in order to distribute the effort required to send requests and thus be able to carry out a more powerful and effective attack.
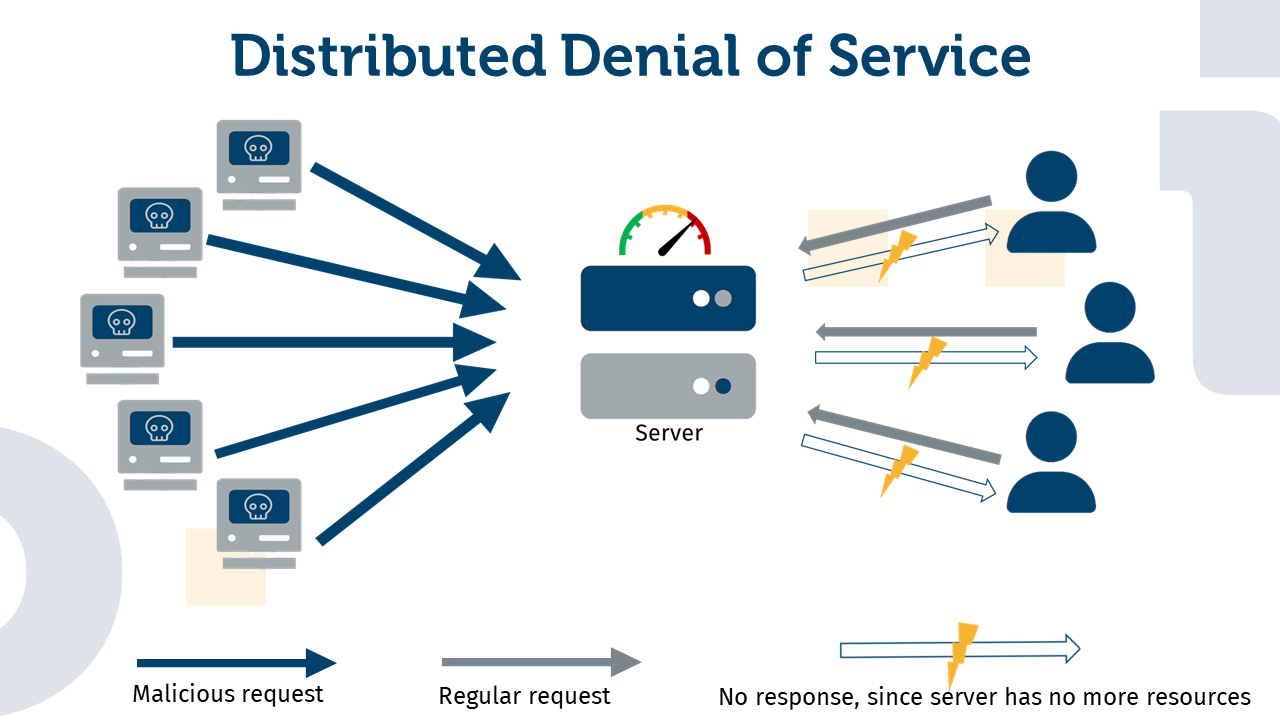
DDoS attacks
A DDoS attack goes one step further than a DoS attack. It involves the use of not just individual attackers, but a multitude of decentralized attackers known as a “botnet.” These botnets consist of compromised computers that are controlled remotely without the legitimate owners knowing. The attacker coordinates the activities of these botnets to flood the target with an even greater number of requests.
An illustrative example of a DDoS attack is a demonstration of protesters in front of a building. A single or a few protesters can easily be controlled by security personnel, this is comparable to a simple DoS attack. General access to the building can usually still be provided, e.g. via other entrances. However, if thousands of people demonstrate in front of all entrances at the same time, the security staff is quickly overloaded and access to the building is blocked. This is an example of a distributed denial of service attack.
Technical background of DDoS attacks
In a DDoS attack, the botnet is used to direct traffic to the target. By distributing traffic from many different sources, the target is flooded with a flood of data packets, causing congestion and making it inaccessible to legitimate users.
The DRDoS Attack - A Small Pebble Can Trigger an Avalanche
A Reflective Denial of Service (DRDoS) attack is a variant of a DDoS attack in which the attacker exploits reflective services or protocols to increase traffic to the target. The attacker sends spoofed requests to these services, which send their responses to the victim. The exploitation of the response packets leads to an exponential increase in traffic that overloads the target.
An example of a DRDoS attack is the use of DNS amplification. The attacker sends spoofed DNS requests to public DNS servers with response packets that are larger than the original request. These oversized response packets are sent to the target instead of the attacker, causing network bandwidth and system resource overload.
Technical background of DRDoS attacks
DRDoS attacks use reflective services or protocols to increase traffic to the target. These services can be public DNS servers, NTP (Network Time Protocol) servers, memcached servers or others. The attacker sends spoofed requests to these services and uses the large response packets to flood the target with significantly more traffic.
Motives for DoS, DDoS and DRDOS Attacks
The motives for the aforementioned attacks can vary widely, but usually play a decisive role in the duration of the attack. Often the attackers have a financial motive and use the attacks to extort a kind of ransom; only after payment of a certain sum is the website or service “released” again. Attacks by “hactivists” on a company are also not uncommon. The attacker demonstrates against poor working conditions or animal testing, for example. Sometimes the attacker represents an ideology, so the attack has more of a political background. In addition, such an attack can also serve merely as a diversionary tactic while attempts are made to gain unauthorized access in order to inflict further damage.
Conclusion
DoS, DDoS, and DRDoS attacks aim to make a resource inaccessible. While a DoS attack is carried out by a single attacker, a DDoS attack uses a botnet of compromised computers, and a DRDoS attack uses reflective services or protocols to amplify traffic. The technical background of these types of attacks is to overload the resource by abusing vulnerabilities, tampering, or resource exhaustion.
It is critical that organizations implement appropriate security measures to protect themselves from such attacks. Here are some concrete safeguards that can protect against both DoS and DDoS attacks, as well as account takeover attacks on administration accounts and user accounts:
Implementation of firewall systems: Firewalls serve as a layer of protection between your network and the Internet. They can monitor incoming and outgoing traffic and block unwanted traffic.
Use intrusion detection and prevention systems (IDS/IPS): These systems monitor network traffic in real time and detect suspicious activity or attacks. They can automatically take action to prevent or block attacks.
Strengthen network infrastructure: Ensure your network components, such as routers and switches, are properly configured and up-to-date with the latest firmware. Implement strong access control lists (ACLs) and authentication methods to prevent unauthorized access.
Regular updates and patching: Keep your systems and software up to date by regularly applying security updates and patches. Vulnerabilities in software can be exploited by attackers to carry out attacks.
Better protect accounts: In addition to implementing strong password policies and using two-factor authentication (2FA), it is important to regularly check for compromised user account passwords. Identeco offers appropriate products that allow you to automatically check your employee and customer accounts for compromise. If a compromise is found, appropriate action can be taken immediately.
Monitor network traffic: implement a monitoring system that continuously monitors network traffic and detects suspicious activity. Early detection can help stop attacks before they cause major damage.
Train employees: make your employees aware of the threats posed by attacks such as account takeover and phishing. Train them in security best practices so they can identify and report suspicious activity.
By implementing and regularly reviewing these safeguards, you can protect your systems and resources from various types of attacks, including DoS, DDoS, and account takeover attacks. It’s important to keep up with the latest developments in cybersecurity and continually improve your security measures to maintain your protection.
Interesting facts about DDoS attacks
- Compared to the previous year, the daily average of DDoS attacks has increased by 150% in 2022. (1).
- The longest DDoS attack last year lasted 66 hours.
- The first DDoS attack took place in 1996. The victim was Panix, an American ISP and the attack lasted almost two days.
- It is believed that the number of DDoS attacks will exceed 15 million this year (2023). (2)


Artikel teilen