Dark Web vs. Deep Web - What can you find there?
- Reading time:
- 4 min

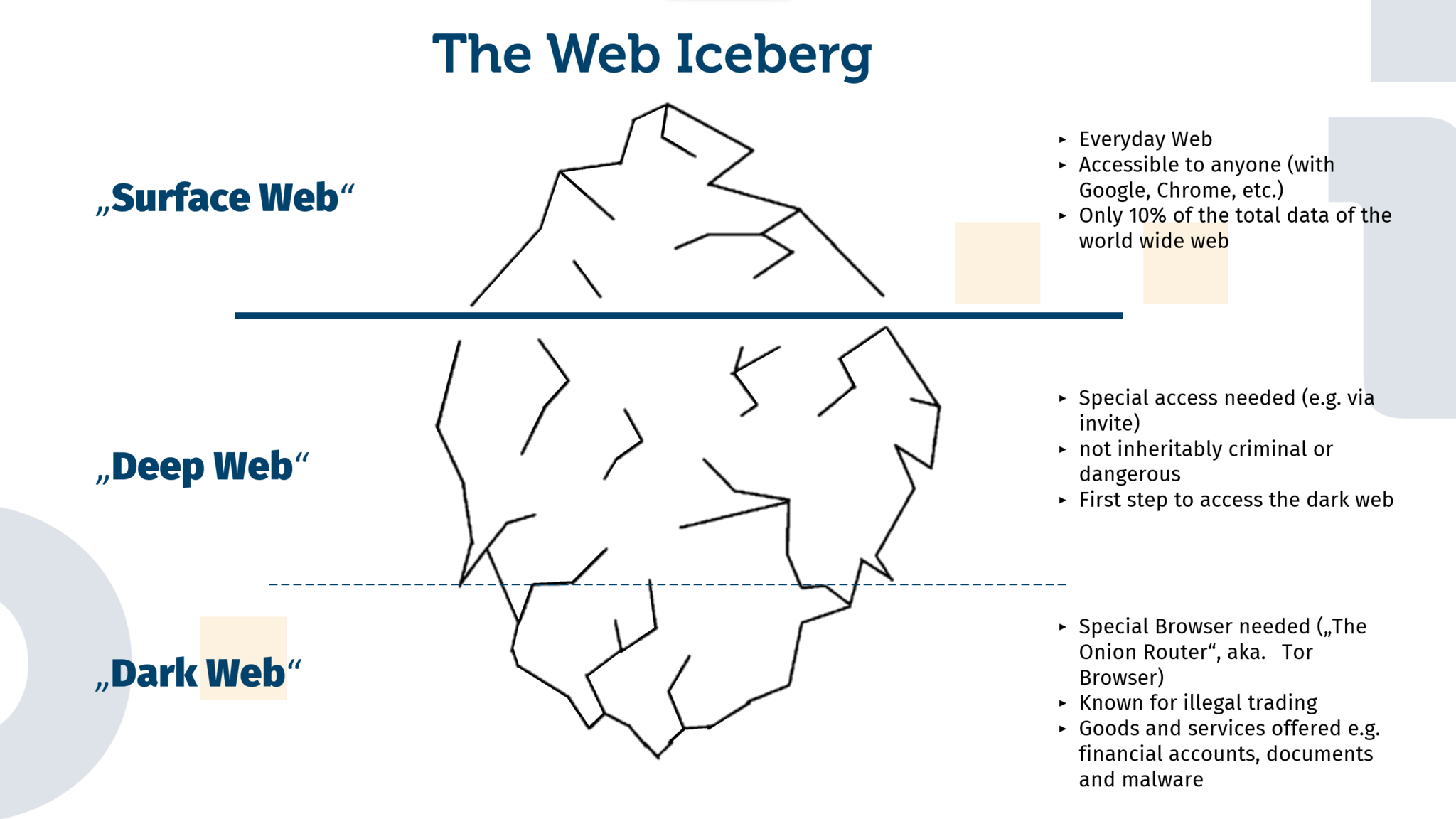
Many have heard of the Dark Web, as it is often depicted in movies and books. But what exactly is it? The regular Internet that people use in their everyday lives belongs to the so-called “Surface Web” and accounts for only 10% of the total amount of data on the World Wide Web. The Deep Web can be thought of as an intermediate layer between the Surface Web and the Dark Web. The Deep Web is characterized in particular by the fact that it cannot or should not be found via classic search engines or directory services. In concrete terms, this often involves platforms such as forums or community boards on which people exchange information in a kind of “closed society”. Copyrighted works (films, music or eBooks) are often exchanged on such platforms. On special themed boards, leaked access data or instructions for hacking are also offered. Entry to these closed societies is usually by invitation and recommendation of a member.
The dark web, on the other hand, is not part of the regular Internet. Access to the separate network is only made possible by using the TOR browser. This browser is used to connect to the so-called Tor network. TOR stands for “The Onion Router” and refers to the software required for access. This connects you to one of several thousand nodes, which then enable switching and data transmission within the Tor network. An important principle within this network is the so-called onion routing, whereby the requesting user remains anonymous to the web server of the requested platform. This is achieved by constantly changing routes via different nodes. This ensures that the user’s identity remains anonymous.
So what exactly can be found on the dark web and who uses it? In short: all sorts of things. As in the Deep Web, there are numerous forums on the Dark Web where you can not only exchange information, but also sell and buy data, accounts and the like. In addition, the range of criminal goods and services on offer is being expanded by weapons, ammunition and instructions on how to build bombs. In addition to these obviously illegal offers of the dark web, the anonymity of the Tor network also protects civil rights activists, journalists and persecuted minorities in countries with restricted freedom of speech. Thus, a blanket condemnation of the technology used for the Tor network would be wrong.
A wide variety of goods and services are offered for payment on both the Deep Web and the Dark Web; here is a small selection:
Darknet Marketplace
- A Netflix account with an annual subscription can be bought for about €25.
- PayPal accounts with a minimum balance of €100 are available for about €10.
- A driver’s license or passport can be purchased in a wide price range. Prices vary depending on the country and whether a digital copy or a (supposed) original is to be sent by mail.
- Stolen bank data and access to online banking.
- Premium malware starting at €5,500 for 1,000 installations. Prices vary here as well, depending on region and promised success rate/lifetime.
For your own protection and to prevent your own accounts or personal information from ending up on the dark web, there are different options.
Protect Your Data While Surfing the Web
- VPN: You can use a VPN yourself when you connect to a public Wi-Fi.
- AV Software: You are highly recommended to install anti-malware/anti-virus software.
- Unique passwords: It is important that you always choose a new password and do not use a variation of existing passwords or even the same password as used on another account.
- Passwordmanager: To keep track of multiple passwords, it is recommended to use a password manager.
- Being skeptical: If you are asked to open a file or provide your personal information, you should always be sure that you are on a safe and legitimate website.
- Know your Enemy: Criminals often get data through phishing, what it is and how you can protect yourself can be found here: Phishing #1: Email Phishing, Baiting and Search Engine Phishing and Phishing #2: CEO Fraud, Corporate Phishing and Angler Phishing Attacks.
If you are worried that your data has been stolen, you can use the Identity Leak Checker from the University of Bonn.
For the protection of employee as well as customer accounts Identeco offers suitable products: Identeco: Our Products.

Artikel teilen