Phishing #2: CEO Fraud, Corporate Phishing and Angler Phishing Attacks
- Reading time:
- 4 min

It is well known that the number of phishing attacks continues to increase. Just like the fact that Germany is one of the countries most affected. The first part of “Phishing, What Is It All About?” covered e-mail phishing, baiting and search engine phishing and explained how to protect yourself from these types of phishing. In this part, CEO Fraud, Corporate Phishing and Angler Phishing Attacks are presented.
CEO Fraud
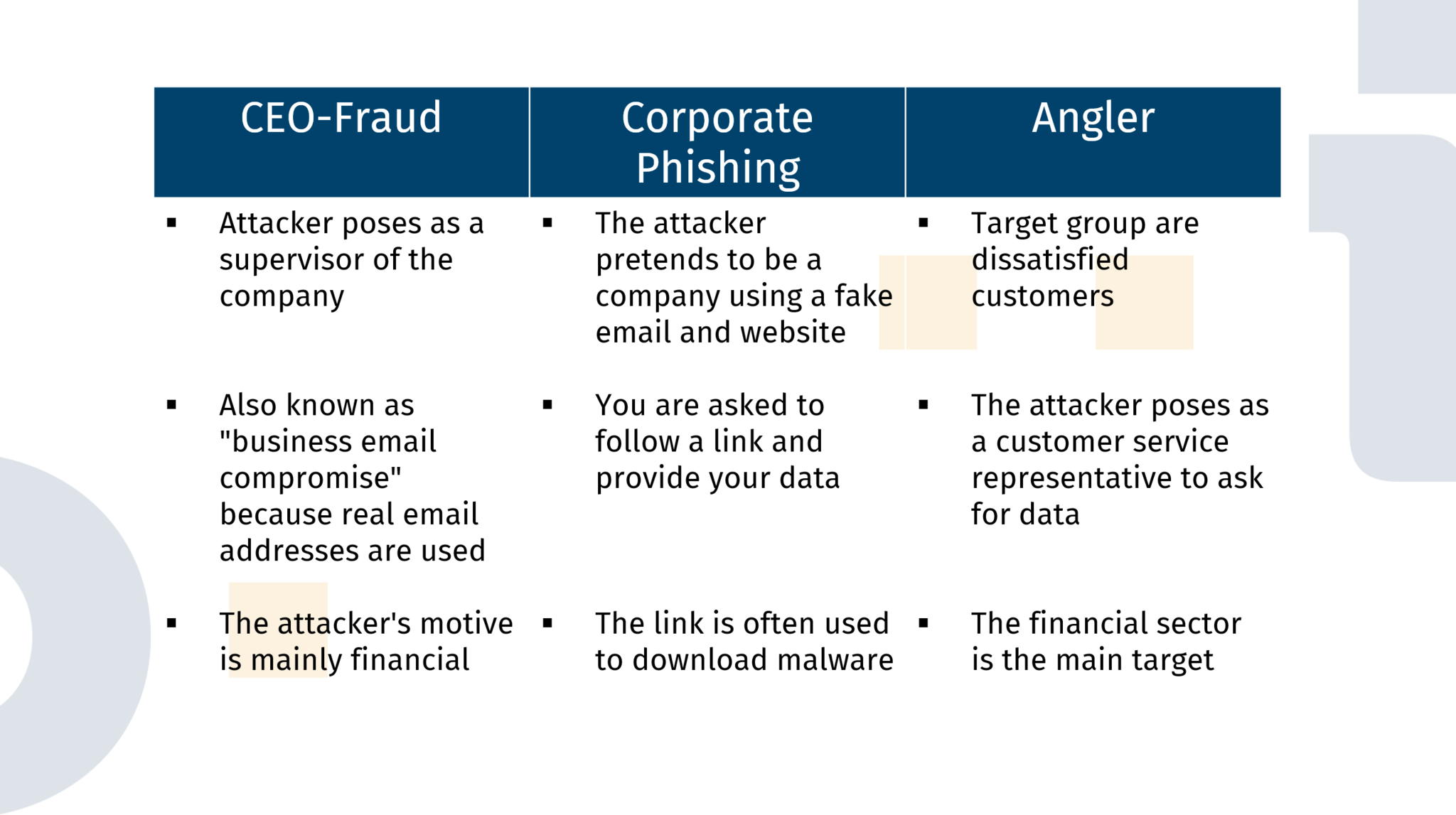
Also known as Business Email Compromise (BEC), this is when email addresses of key people within a company, such as the CEO, have been captured. The attacker sends emails to employees pretending that an amount of money is to be transferred. Often the situation is presented as very seriously so that the employee is urged to care and has less chance to think about it and directly carries out the activity. It is important here to not confuse “CEO Fraud” with “Corporate Phishing”, because in “CEO Fraud” real existing email addresses are used and the motivation of the attacker is in most cases purely financial.
How can you ensure not to be tricked by something like this when the real email addresses of your superiors are used?
- You should first ask yourself whether the situation presented is a realistic one for your company. Then you should consider whether the requested amount seems suspicious. If you wonder to whom the money is to be transferred, perhaps this is also suspicious.
- The attacker might not be 100% familiar with your company’s internal regulations, so it may be that the email of a superior is used, with whom you do not actually come into contact. If this is the case, you should contact your own supervisor.
- If the email is supposed to be from your own supervisor, you can also recognize a phishing attack by the wording. Are words used that the person doesn’t actually use? Is the wording of the request different to other instances?
Above all, it is important not to get stressed and rather question the legitimacy for some time and inform other supervisors instead of going straight into it and make a mistake.
Corporate Phishing
Unlike CEO Fraud, the email addresses are totally made up but should be similar enough to the real addresses that you can’t tell the difference. This type of phishing is very similar to common email phishing with the biggest difference being that the attackers make great effort to let the mailing appear pretty real. This means that the content of the emails is supposed to come across as legitimate as possible, including the company’s logo and the request to interact with the link. This link then leads to a website that appears similar to the real company website. Here, you are requested to login with valid credentials or perhaps enter banking details. With this type of phishing, the motivation is rarely just financial. Regularly, malware is downloaded in the background or the credentials are collected for later use for example in an Account Takeover Attack.
- To avoid falling for this kind of phishing attack, you can start by asking yourself the same questions you would ask in an email phishing attack: Are the sender’s name and address spelled correctly? Are there any differences from the sender addresses used in other emails? Is the content logical and correct?
- Before following a link, take a look at the address behind the link. Is there anything conspicuous? Has the name been misspelled or is the ending different, e.g. .com is used instead of .de?
- If you still land on the suspicious website, you can check if something noticeable has been changed. Perhaps the background color is different or the font used is inconsistent.
Angler Phishing Attacks
The target audience of this phishing attack are dissatisfied customers. When someone leaves a bad review, the attacker will impersonate a customer support agent and pretend to assist with the problem. In doing so, they will try to find out more information about the customer to use it later on. The most affected institutions are in the finance sector, so the motivation of the attack here seems financial.
To avoid such a phishing attack, you should pay attention to the following:
- How recent is your complaint or rating? Has the problem already been solved or has one already been approached about it?
- On which way are you being contacted? Perhaps something is already phishy e.g. the e-mail address itself or the wording used. Was everything spelled and formulated correctly?
- Is there a connection between the information you are asked for and what you have complained about earlier? Is the way of communication safe to share sensitive data?

Artikel teilen